TECHNICAL REPORT
| Grantee |
National Electronics and Computer Technology Center (National Science and Technology Development Agency)
|
| Project Title | Open-source SOC-as-a-Service for Strengthening Cybersecurity in Small and Medium Manufacturers in Thailand toward Industry 4.0 |
| Amount Awarded | USD 30,000 |
| Dates covered by this report: | 2023-01-01 to 2024-04-30 |
| Report submission date | 2024-05-01 |
| Economies where project was implemented | Thailand |
| Project leader name |
Panita Pongpaibool
|
| Project Team |
Tinthid Jaikla
Kalika Suksomboon
Montida Pattaranantakul
|
Project Summary
Cyber attacks in manufacturing had proliferated across the globe, raising concerns about whether Thai manufacturing should move toward Industry 4.0. Promotion of Industry 4.0 transformation often recommended digital technologies such as cloud computing, data analytics, and the Internet of Things. Cybersecurity, though an essential component, was not addressed as much in the context of Industry 4.0. Strengthening cybersecurity in manufacturing meant securing not only the IT (information technology) infrastructure but also the OT (operational technology) components such as machines, controllers, and shop-floor facilities. To prevent and reduce the impacts of cyber attacks in a factory setting, a complex real-time monitoring and evaluation of cyber risks were necessary. Because the industrial communication protocols consisted of both proprietary and open standards, typical cybersecurity software tools, which were suitable for a normal IT/enterprise environment, might not have been sufficient to monitor communication and data transfer among factory machines. While large manufacturers could invest in such complex security prevention services, either internal or outsourced, small and medium manufacturers could not afford to invest in either internal or outsourced cybersecurity services. This gap in cybersecurity affordability created a kind of digital divide, which was not healthy in today’s global supply chains where large and small manufacturers must rely on one another.
This project aimed to develop a Security Operations Center (SOC) to support small and medium factories in Thailand. We tried to implement it with all open-source software to reduce development and operation costs, making this service sustainable and affordable for SMEs. In this project, we tested our SOC services with three small and medium-sized factories. These factories received standard SOC services: cybersecurity monitoring, incident response, vulnerability assessment, and threat analysis for at least three months. We fine-tuned our SOC operations and services based on feedback from these factories. The result of this project was a prototype SOC-as-a-service that could scale out to serve more factories in Thailand. Additionally, we provided cybersecurity awareness training to factory personnel as well as system integrators and developers of Industry 4.0 solutions.
Table of Contents
- Background and Justification
- Project Implementation Narrative
- Project Activities, Deliverables and Indicators
- Project Review and Assessment
- Diversity and Inclusion
- Project Communication
- Project Sustainability
- Project Management
- Project Recommendations and Use of Findings
- Bibliography
Background and Justification
According to the Thailand Board of Investment, in 2022 Thailand's manufacturing output was ranked 18th worldwide. It was ranked the world's 25th largest exporter. Moreover, Industrial output qualified Thailand for a 21st place ranking. In fact manufacturing contributes to as much as 33% of Thailand GDP in 2020. However, over the past 10 years the GDP contribution by manufacturing has been declining (from 40% in 2010 to 33% in 2020).
The Federation of Thai Industry surveyed the maturity and competitiveness of 1,335 Thai manufacturers in 2021 and found that 70% of them have development maturing below industry 3.0 (2% Industry 4.0, 28% industry 3.0, 61% Industry 2.0, and 9% Industry 1.0). When we explored further to understand the gap of development, we found that the dimensions that are the most lacking in many factories are facility and production connectivity. Even though many factories have networks and IT infrastructure, they are usually limited to enterprise and business usage. Shop floors, production lines, and facilities are lacking behind in digital infrastructure. In addition, cybersecurity, though one of the key components of Industry 4.0, is usually overlooked by factory owners. It is probably because of lack of personnel, high investment, and not creating direct value to production. As more factories are adopting Internet of Things (IoT) as tools to monitor machine and production status, more Internet traffic is generated from shop-floors. Network endpoints are no longer computers and servers, but IoT devices, microcontrollers, and PLCs (Programmable Logic Controllers). These endpoints usually have limited processing power. Anti-virus software and typical cybersecurity protection are not feasible options. Therefore, proper cybersecurity protection is essential to help factories guard against cyber attacks in shop-floors as well as in enterprise networks.
The Security Operation Center developed in this project will offer essential infrastructure and services to factories in the EEC area. Improvement of cybersecurity in factories will improve production reliability and resiliency, ensure business and production continuity, increase trust in the supply chain, and in turn increase their global competitiveness. Bringing these factories a step closer toward Industry 4.0 maturity through cybersecurity capacity is the goal of this project.
A Security Operations Center (SOC) comprises people, processes and technology working cooperatively around the clock to ensure timely response to cyber incidents. With the real-time log analysis, malicious activities can be detected and responded to in real-time. The root cause is identified to eliminate future risks. Alerting policy and response plan must be defined with clear roles and constructive action plans to ensure incidents can be promptly handled. However, deploying SOC requires a large investment in developing skilled personnel and purchasing software licenses. Large-scaled factories with enough budget may opt to build an in-house SOC or may offload the complexity by outsourcing the service. Despite its benefits, SOC services are not affordable for small and medium-sized factories. As a result, these factories just leave the cybersecurity aside and just hope that they are not attack targets.
Ideally, each factory, large or small, should have a dedicated SOC service. With this goal in mind, our team of cybersecurity researchers set out to explore options to provide low-cost SOC services to Thai factories. Instead of encouraging factories to set up on-premise SOCs, we opt to set up a centralized SOC-as-a-service. With this SOC-as-a-service, factories can get protection on a pay-per-use basis without worrying about equipment and human investment. In order for this centralized SOC to sustainably provide affordable, low-cost services, we intend to set it up with all open-source software tools. The challenging part of this is to design the right level of protection service (not full-fledged service) suitable for small and medium factories. Training of our SOC operators and related factory personnel is essential to ensure sustainability of this proposed service.
Project Implementation Narrative
Prototype SOC Development
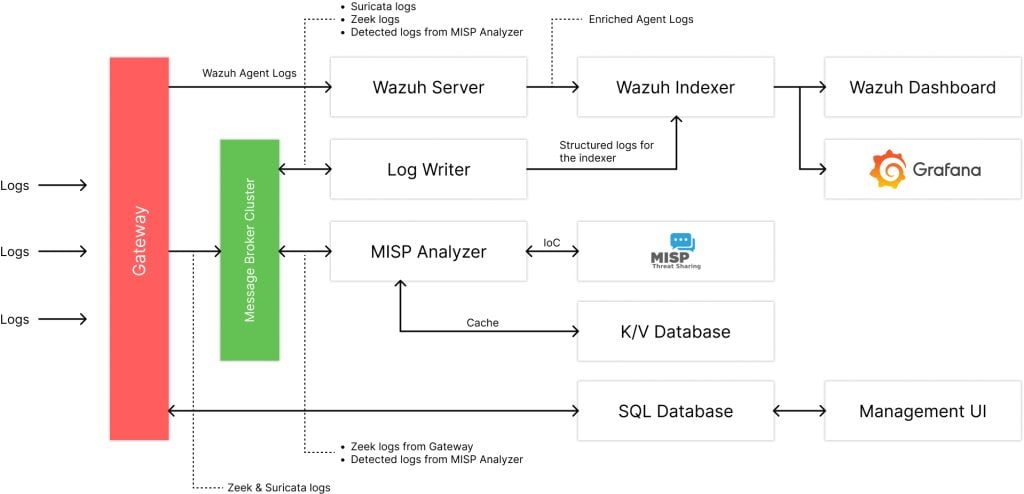
There are two parts to our SOC architecture: one on the factory’s premise and the other on the cloud. Server logs and network traffic are collected at each factory’s site and sent out to our SOC-as-a-service cloud. Our SOC-as-a-service performs log processing, data storage, threat intelligence, visualization, and alerts. A set of open-source software is selected for these SOC functionalities. Additionally, we have designed a new service that integrates with the APIs of the open-source tools we use. This service makes it easier to oversee and manage systems to support the multi-client environments. Our architecture is designed for easy scalability, both upwards and downwards, by employing a message bus and decoupling services based on their tasks. The resulting open-source SOC-as-a-service architecture is illustrated in Figure 1 and Figure 2.
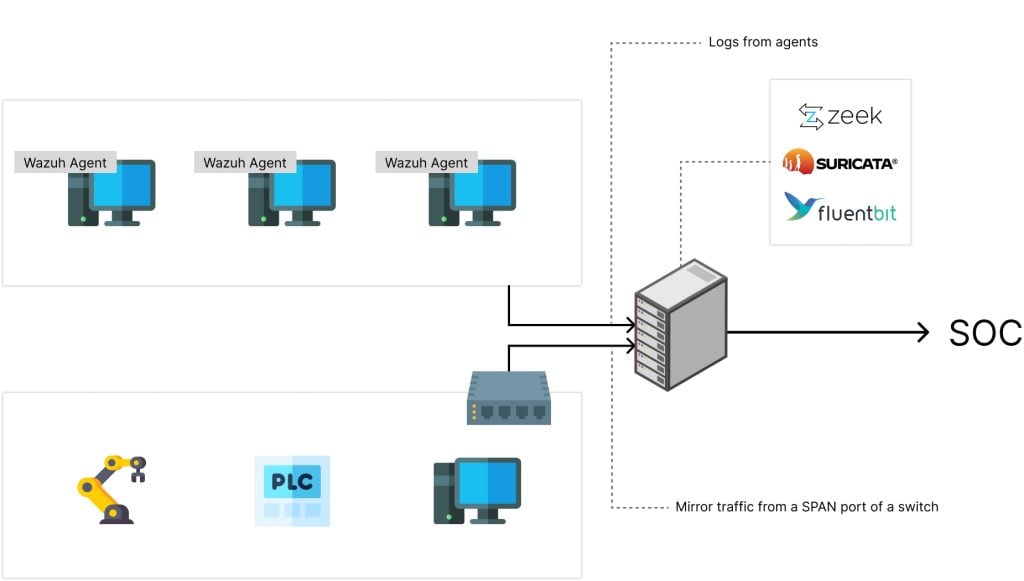
We will describe how our SOC works, beginning with our method for collecting logs from client networks and machines. After collection, we'll cover how these logs are processed and securely stored. Then, we'll explain the role of our threat intelligence platform in enhancing these logs with additional insights. Finally, we'll show how we use an open-source dashboard for effective data visualization and alert generation.
1. Log collection
We collected two types of logs: one from the client’s endpoints, like workstations and personal laptops, and the other from analyzing network traffic. The logs from endpoints are collected by installing an agent on the endpoints to collect system logs, event logs, or even registry changes. Network traffic is gathered from network devices equipped with SPAN port functionality, such as switches. These network traffic logs are then analyzed by a server, which can be called a sensor, we have deployed at the client site.
For agent deployment, we chose Wazuh Agent, a host-based intrusion detection system. Wazuh Agent is instrumental in gathering security events, system logs, configuration changes, and spotting behavioral anomalies on the endpoints we monitor.
On the network traffic analysis side, we use Zeek, Suricata, and FluentBit. Zeek extracts files from network flows and executes scripts based on network events. Zeek has plugins that are customized to work with OT protocols. The structured logs generated by Zeek are written into files, which are then read by FluentBit before sending to the SOC's gateway. In addition to Zeek, we use Suricata as a network intrusion detection system. Suricata receives network traffic and compares the traffic pattern with the defined rules. If Suricata detects traffic that violates these rules, it will generate an alert in its log.
2. Log Processing and Databases
The processing of the logs can be divided into two parts, as the logs from agents and sensors are processed in different pipelines.
2.1. Agents: Wazuh agents send logs to the Wazuh server as normal. This server analyzes the data, raises alerts for detected threats or anomalies, and manages agent configurations and monitoring. This information from the Wazuh server is then stored in the Wazuh Indexer.
2.2. Sensors: At the gateway, the keys attached to logs from sensors are authenticated by comparing them with valid keys. This method enables support for multiple clients. After validation, the Zeek logs are sent to the message broker, NATS, to be received by the threat intelligence analyzer for detecting malicious IoCs. Meanwhile, Suricata logs are directed to the service that writes the logs to the Wazuh indexer.
3. Threat Intelligence
We chose MISP as our threat intelligence platform, which leverages various open-source intel feeds. We developed a service that subscribes to every log type from Zeek via the message broker. This service extracts Indicators of Compromise (IoCs), such as file hashes, IP addresses, and domain names, and checks them against MISP through an API to determine if they are malicious. If malicious IoCs are detected, they are logged in the Wazuh Indexer, enabling the generation of alerts.
4. Visualization and Alerting
Continuing with the use of the Wazuh platform, we employ the Wazuh Dashboard to fetch data from the Wazuh Indexer. SOC analysts can use the Wazuh Dashboard to investigate alerts generated by the Wazuh agents. Additionally, the Wazuh Dashboard is also used for Zeek and Suricata. Although the Wazuh Dashboard offers a multi-account feature, it lacks support for a view-only guest mode. Therefore, we chose Grafana as an alternative for creating dashboards for clients (factory personnel) to view data without having permissions to alter configurations.
We utilize the functionality provided by the Wazuh Dashboard for creating alerts. Alerts can be sent to messaging platforms such as Slack or email. We set up alert conditions based on the logs received from the data processing pipeline, threat intelligence, or other detection services.
Project Activities, Deliverables and Indicators
Beginning of Project
| Activity | Description | #Months |
|---|---|---|
| Overview of security status in factories in EEC | Analyze the cybersecurity ecosystems status in order to assess the main opportunities for developing a SOC service for improving the cybersecurity posture of SME factories in the EEC area | 1 |
| Pilot factory selection | Survey the need for SOC and readiness and willingness to participate in this project. Select 3 pilot factories. | 2 |
Middle of Project
| Activity | Description | #Months |
|---|---|---|
| Pilot service with the 3 factories | Provide SOC service to 3 pilot factories. | 4 |
| Training program | Conduct a formal training course on SOC to selected SMEs and a course on cybersecurity awareness to system integrators and related EEC personnel. | 2 |
End of Project
| Activity | Description | #Months |
|---|---|---|
| Documentation | Develop technical report and guidelines for implementation and best practices for SOC operators and for factories | 3 |
| Project results evaluation | Evaluate the implementation of the open-source SOC deployment in terms of cost-benefit, feasibility to scale to serve more factories, and impact assessment. Write the final report. | 2 |
Throughout the Project
| Activity | Description | #Months |
|---|---|---|
| Implement the open-source SOC service | Provide practical methods in SOC development using open-source. Configure and implement software and processes for SOC. PDCA (Plan-Do-Check-Act) the system and operation as it runs pilot service. | 9 |
Key Deliverables
| Deliverable | Status |
|---|---|
| Survey and select the factory candidates | Completed |
| Implement SOC as a Service prototype #1 | Completed |
| Implement SOC as a Service prototype #2 | Completed |
| Implement SOC as a Service prototype #3 | Completed |
| Implement SOC as a Service prototype #4 | Completed |
| Prototype Installation and Implementation | Completed |
| Write report of best practices | Completed |
| Project result evaluation | Completed |
| Awareness seminar | Completed |
| Workshop | Completed |
Key Deliverables - Detail
| Deliverable: Survey and select the factory candidates Status: Completed Start Date: February 1, 2023 Completion Date: March 3, 2023 Baseline:No factory candidate Activities: Currently, there are over 7,000 factories in Thailand, of which ninety-six percent are small and medium-sized. Thus, this project aims to pilot at three small and medium-sized factories. The criteria for selecting these pilot factories are as follows: 1) Small or medium-sized [according to the definition of the Office of SMEs Promotion Thailand], 2) Top-down awareness, 3) Willingness to experiment with new technologies, 4) Dedicated IT team. Finally, we selected three pilot factories for implementing the SOC service: 1) Thai Herbal Products Co., Ltd., 2) The Pet Co., Ltd., and 3) GravitechThai (Thailand) Co., Ltd. Thai Herbal Products Co., Ltd. [https://www.thaiherbinfo.com/en] Thai Herbal Products Co.,Ltd. has produced herbal products since 1999 in phytopharmaceutical style under Herbal Medicinal Products of GMP standard and ISO 9001 version 2008. Manufacturing technology was transferred from Research and Development Institute of the Government Pharmaceutical Organization. The company is a specialist in capsule, tablet, cream, gel, oral liquid and aroma technology. The Thai Herbal Products Company factory is located at Wang-Chula industrial estate in Ayuthaya province. Its main activity is producing herbal medicines and health food supplements, under the GMP. The number of products manufactured at present is 22 items. Address: 130/149 Moo 3 Wangchula, Ayutthaya, 13170 Thailand Tel : 035-721445-7, 063-2049077-8 The Pet Co., Ltd. [https://www.thepetco.com/ ] The Pet Co., Ltd. was established in 1994 to produce PET (Polyethylene Terepthalate) bottles for the food and beverage industry and PP board for the stationery and packaging industry. Address: 23/4 Moo 2 Pathumthani-Ladlumkaew Rd., Ban Chang, Muang, Pathumthani 12000 Tel: 02-581-7950-3 Thanakorn Vegetable Oil Products Co., Ltd. [https://www.cook.co.th/en/home] The company was established in Phra Samut Jehdi District, Samut Phrakarn Province. Today, the company's production capacity is 2,500 tons of soybean per day. Its products include vegetable oil and animal feed ingredients. Address: 99 Moo.2 Soi Thanakorn Phrasamutjedi Road, Pak Khlong Bang Plakod, Samutprakarn ,10290 Tel: 02-819-7470 Outcomes: 1. Three pilot factories have been selected and have agreed to participate: 1) Thai Herbal Products Co., Ltd. 2) The Pet Co., Ltd. 3) Thanakorn Vegetable Oil Products 2. Three non-disclosure agreements were established. Additional Comments: Survey the need for SOC, as well as the readiness and willingness to participate in this project. Select three factory candidates for participation. This candidate selection should be completed within the first month of the project. |
| Deliverable: Implement SOC as a Service prototype #1 Status: Completed Start Date: February 1, 2023 Completion Date: April 30, 2023 Baseline:Begin with no prior knowledge of tools and the implementation of logging services Activities: Surveys open-source software tools related to central log management and processing pipelines. The tools include Fluentd, Fluent Bit, Graylog, Apache Kafka, Rsyslog, Suridata, Elasticsearch, Logstash, and Wazuh. Outcomes: Selected Open-Source Software Tools. The selected open-source software tools are as follows: Log Collection: - Wazuh Agent: Chosen for host-based intrusion detection. - Zeek, Suricata, and FluentBit: Selected for network traffic collection and analysis. Log Processing and Databases: - Wazuh Server: Chosen for data analysis, alerting, agent configuration management, and monitoring. Log Indexing: - Wazuh Indexer: Used for indexing log data, enabling efficient search and retrieval. This tool facilitates the organization of log data into searchable indexes, allowing for quick access and analysis of security events and alerts. Additional Comments: Logging Database and Processing Pipeline The development of the logging database and processing pipeline will be carried out during the 2nd to 4th months of the project. The components of this pipeline are as follows: Logging Database: The logging database is designed to store structured logs sent from the log aggregator. These logs must be searchable, filterable, and capable of integration with visualization platforms via an API. Additionally, the logging database must have the ability to scale up or down in response to log traffic and data volume. Log Aggregator: The log aggregator's role is to aggregate data from various devices provided by the log collectors. It must extract details from unstructured data, transform them into structured logs, and then forward these logs to the logging database. Log Collector: The log collector is installed on devices or servers to capture all security-related data. This data is then sent to the log aggregator. The log collector must be capable of capturing data useful for threat monitoring, such as network logs and system logs. |
| Deliverable: Implement SOC as a Service prototype #2 Status: Completed Start Date: April 1, 2023 Completion Date: May 31, 2023 Baseline:Starting with no prior knowledge of threat intelligence tools Activities: We surveyed open-source tools related to threat intelligence, including MISP, OpenCTI, CIF, CRITs, and IntelOWL. Outcomes: MISP has been selected for threat intelligence in this project. MISP was chosen for threat intelligence due to its robust capabilities in sharing, storing, and correlating indicators of compromise (IoCs) of targeted attacks, threat intelligence, and financial fraud. MISP facilitates the efficient exchange of threat data among organizations, enhances detection and prevention of security incidents, and supports the automation of threat intelligence processes. Additionally, its extensive community support and continuous updates make it a reliable and effective tool for maintaining up-to-date threat intelligence. Additional Comments: Threat Intelligence Platform. The development of the threat intelligence platform will be carried out during the 4th to 5th months of the project. This platform will gather log data from the logging database and compare it with threat intelligence feeds or APIs provided by third-party providers. The threat intelligence platform will support threat identification from various types of information, including: - IP (Inbound/Outbound) - Domain - URL - File hash |
| Deliverable: Implement SOC as a Service prototype #3 Status: Completed Start Date: May 1, 2023 Completion Date: June 30, 2023 Baseline:Starting with no prior knowledge of visualization tool. Activities: We surveyed open-source tools related to data visualization, including Apache Superset, Grafana, Metabase, Kibana, and OpenSearch. Outcomes: The selected open-source software tools for data visualization are as follows: Grafana: Although the Wazuh Dashboard offers a multi-account feature, it lacks support for a view-only guest mode. Therefore, we chose Grafana as an alternative for creating dashboards for clients (factory personnel) to view data without having permissions to alter configurations. OpenSearch: OpenSearch is suitable for searching, visualizing, and analyzing data, making it a good fit for creating detailed dashboards and reports. Additional Comments: Data Visualization Dashboard. The development of the data visualization dashboard will be carried out during the 5th to 6th months of the project. This interactive dashboard will add visualization, correlation, and alerting capabilities, providing a quick overview of all cybersecurity-related events within the factory's environment. It will aggregate data from the threat intelligence platforms and the logging database to highlight potential threats occurring in the systems. The dashboard will provide the following information: 1. Overall risk level 2. Network and system events/incidents 3. Common indicators of compromise (IoC): 3.1 Unusual network traffic 3.2 Geographical irregularities 3.3 Unusual login attempts 3.4 Suspicious registry or system file changes 3.5 Indicators of DDoS attacks 4. Potential threat information provided by the threat intelligence platform |
| Deliverable: Implement SOC as a Service prototype #4 Status: Completed Start Date: May 1, 2023 Completion Date: June 30, 2023 Baseline:Starting with no prior knowledge of alerting service tools Activities: We surveyed open-source tools related to alert services, including ElastAlert, Alertmanager, and Shinken, Wazuh alert via webhook API. Outcomes: Alerting system: We utilized the functionality provided by the Wazuh Dashboard to create and manage alerts. This allowed us to set up alert conditions based on logs received from the data processing pipeline, threat intelligence platforms, and other detection services. The alerts were configured to be sent to various messaging platforms, such as Slack, as well as through email. This setup enabled us to promptly respond to high-risk threat incidents and ensure that key personnel were informed of critical security events in real time. Additional Comments: Signal Alerting Service. The development of the signal alerting service will be carried out during the 5th to 6th months of the project. This service will send notifications based on the identification of high-risk threat incidents. The signal alerting will provide alerts via webhook API and email. |
| Deliverable: Prototype Installation and Implementation Status: Completed Start Date: September 1, 2023 Completion Date: December 31, 2023 Baseline:One of the factories has proper network equipment that can support our log collector installation. However, the remaining factories lack sufficient network equipment and detailed network architecture necessary for supporting the installation. Activities: We started discussing with 3 factories to learn about their network configuration and to prepare necessary equipment for installing our tools at the factories such as switches and servers. Outcomes: Our prototype has been installed at three factories. The logs from all sites have been successfully transmitted to our cloud platform. Additional Comments: Prototype Installation and Implementation during the 7th-9th month of the project. Install the open-source SOC prototype in the selected 3 SME factories in Thailand for at least 3 months. The data feeds from the IT system of factories to the prototype. The POC of this prototype will be evaluated by the IT/network engineers of the factories. |
| Deliverable: Write report of best practices Status: Completed Start Date: October 1, 2023 Completion Date: May 15, 2024 Baseline:Starting with no prior knowledge of the best practices. Activities: By combining the initial review, the development and implementation process, and the insights gathered from our ongoing experiences and incident reports, we have established a set of best practices that can be used to guide future projects in similar contexts. These best practices ensure a structured approach to implementing SOC services using open-source tools, while also providing a framework for continuous improvement and adaptation based on real-world experiences. (See our full report for more detail) Outcomes: The best practices report has been concluded in the full report. This report outlines the best practices developed during the project, starting from the initial review of open-source tools, through the development and implementation of our prototype, and including insights gathered from our experience and monthly incident reports. Additional Comments: Create report of best practices in operational cybersecurity from our experience with the 3 pilot factories. Develop technical report and guidelines for implementation and best practices for SOC operators and for factories. To be done during the 10th-12th month of the project. |
| Deliverable: Project result evaluation Status: Completed Start Date: March 30, 2024 Completion Date: June 15, 2024 Baseline:The results of our project by comparing our open-source SOC implementation to commercial SOC solutions and analyzing the cost differences between using open-source tools and commercial counterparts. Activities: We conducted a survey to understand the cost associated with commercial SOC solutions. This survey included examining licensing fees, subscription costs, and any additional expenses related to support and maintenance. Outcomes: The report of the result evaluation includes detailed findings that demonstrate the project was successful in showing that an open-source SOC can be a viable and cost-effective alternative to commercial SOC solutions, particularly for small and medium-sized enterprises with limited budgets. Additional Comments: Evaluate the implementation of the open source SOC deployment in terms of cost benefit, feasibility to scale to serve more factories, and impact assessment. Write the report during the last 2 months of the project. To be done during the 11th-12th month of the project. |
| Deliverable: Awareness seminar Status: Completed Start Date: January 1, 2024 Completion Date: February 5, 2024 Baseline:We have partnered with factories in Thailand, particularly in the EEC area. Additionally, we have experience in conducting knowledge-sharing activities related to cybersecurity but not about SOC. Activities: As part of our project commitment, we organized a cybersecurity awareness seminar with the goal of attracting at least 200 participants from 7 different organizations. This seminar took place on February 5, 2024, at True Digital Park, the location of True Digital's Security Operations Center (SOC). The seminar exceeded our expectations, drawing over 200 attendees who represented various organizations. Throughout the event, participants were educated on several key areas. They learned the basics of cybersecurity specifically tailored for factories, also known as operational technology (OT) security. In addition, we introduced them to our open-source SOC software suite, explaining its features and benefits. Furthermore, the seminar included insights from our pilot factories, sharing real-world experiences and lessons learned from implementing the SOC software. One of the highlights of the day was the opportunity for attendees to visit True Digital’s SOC, giving them a firsthand look at how a commercial SOC operates. The event featured eight main sessions covering a range of topics, along with a dedicated timeslot for the SOC visit. To enhance the learning experience, we provided downloadable resources such as presentation slides and workshop handouts. Our seminar was well-documented and shared on social media platforms, allowing for wider dissemination of the knowledge and experiences gained during the event. You can find more details and updates about the seminar on our Facebook Post 1 [https://www.facebook.com/share/p/FdAnNmdoHYwbwMdi/?mibextid=oFDknk ] and Facebook Post 2 [https://www.facebook.com/share/p/b685jqfrbTLPSuVL/?mibextid=oFDknk]. Overall, the seminar was a significant step forward in raising cybersecurity awareness and equipping participants with the knowledge and tools to improve their security practices. Outcomes: More than 300 people attended the seminar onsite. 7 organizations exhibited their products and services. 1. Sustainable Manufacturing Center 2. True Digital Group 3. National Cyber Security Agency (NCSA) Thailand 4. Fortinet Security Network (Thailand) 5. T-NET IT Solution 6. Paloalto Networks (Thailand) 7. IRC Technologies We would like to acknowledge True Digital Group for providing their auditorium and arranging the SOC visit. Additional Comments: Organize a 1-day seminar to create cybersecurity awareness among factories and related industries. |
| Deliverable: Workshop Status: Completed Start Date: April 1, 2024 Completion Date: April 29, 2024 Baseline:This activity was not part of the original plan. It was added after the seminar due to significant interest from many companies in using the software developed in this project. Consequently, we decided to conduct a training session. Activities: Activities of This Training Event: 1. Introduction to SOC Software Suite: - Overview of the SOC software suite developed during the project. - Explanation of its key features and capabilities. 2. Installation Guide: - Step-by-step instructions on installing the SOC software suite. - Hands-on installation practice for participants. 3. Configuration Setup: - Detailed guidance on configuring the software to meet specific security needs. - Customization options and best practices for configuration. 4. Operational Procedures: - Training on how to operate the SOC software suite. - Real-time monitoring and incident response procedures. 5. Troubleshooting and Maintenance: - Common issues and solutions. - Maintenance tips to ensure optimal performance. 6. Interactive Q&A Session: - Open floor for participants to ask questions. - Discussions on specific use cases and scenarios. 7. Practical Exercises: - Hands-on exercises 8. Feedback Collection: - Gathering feedback from participants on the training session. Outcomes: Outcome of the Training Event includes: 1. Workshop Documents: - Detailed installation and configuration guides. - Step-by-step operational procedures. - Troubleshooting and maintenance manuals. - Presentation slides and handouts from the training sessions. 2. Feedback from Workshop Participants: - Collected feedback on the effectiveness and clarity of the training. - Insights and suggestions from participants for further improvements. - Assessment of participants' confidence and readiness to use the SOC software suite. Number of Participants includes 18 attendees from 6 companies. Additional Comments: We conducted a half-day workshop to train security providers on how to install, configure, and operate the SOC software suite developed during this project. |
Project Review and Assessment
Overall, the project went as planned. Some initial findings are that it is very challenging to convince factories that their OT infrastructure needs cybersecurity protection. When we invited them to test out our SOC platform, many refused due to fear that our program will look at their sensitive manufacturing data or fear that it would disrupt normal work procedures. While many opted not to participate in our pilot test, we managed to find three factories that are willing to experiment (although we feel that they were also hesitant). We are grateful to them. However, it is not all that smooth. There was a time when a factory's Wi-Fi stopped working and they asked us to turn off our agents. Even though it was not related, the factory readily believes it was because of our system. Therefore, we started to see that it will be challenging to scale up our SOC-as-a service platform to serve more factories when cybersecurity awareness and understanding is still low among SME factories.
After finishing the pilot test, we organized a one-day seminar targeting factories and automation system integrators. This seminar was very well received as it was a rare event that brought up the OT security awareness. This seminar brought together IT/security professionals to meet with manufacturing professionals. During the seminar our team got a first-hand experience inside the commercial SOC and learned the process of building SOC from a large bank. We realized that our open-source SOC developed in this project is still far from the commercial one. Especially one lacking feature is threat intelligence which is the heart and soul of a SOC service. The open-source threat intelligence is sufficient but cannot combat zero-day attacks.
Our seminar was honored to host the director of Thailand’s NCSA (National Cyber Security Agency). It also results in a close relationship among our organization and NCSA (National Cyber Security Agency). An MOU was signed between the two organizations and we collaborated on writing a project proposal to disseminate the open-source SOC for nation-wide utilization.
Diversity and Inclusion
This project supports active participation of women in our team members. In fact, more than half of our team members are women.
In our seminar, there were 29% female participants (59 out of 204 participants). Out of 10 speakers, three were female speakers. It is inspiring to see a female executive heading the True Digital Security business, who is also our supporting partner for this seminar.
Project Communication
In the original proposal, we planned to communicate this project through a 1-day awareness seminar. Along the way, we got many opportunities to communicate this project as follows.
- AINTEC 2023
We presented our work titled “On the Design and Development of Low-Cost SOC-as-a-Service for Industry 4.0” at the Asian Internet Engineering Conference 2023 in Hanoi Vietnam during 12-14 December 2023. Information about AINTEC 2023 https://interlab.ait.ac.th/aintec2023/ - APAN 57
Our team member, Dr.Chalee Vorakulpipat, presented “Open Source SOC Service: Strengthening Cybersecurity for Smart Manufacturing in Thailand” under APAN Security Working Group at APAN (Asia-Pacific Advanced Network) 57 in Bangkok Thailand. - Cyber Security : Foundation for Industry 4.0 Seminar
This project committed to organize one cybersecurity awareness seminar with at least 200 participants. Our seminar was held on February 5, 2024 at True Digital Park. (Location of True Digital’s SOC) More than 200 participants attended the seminar where they learned about basic cybersecurity for factories (OT security), about our open-source SOC software suite, about SOC experience from our pilot factories, and got first-hand experience visiting inside True Digital’s SOC.We would like to acknowledge True Digital Group for providing their auditorium and allowing participants to visit their SOC. (Note: We would like to acknowledge True Digital Group for providing their auditorium and allowing participants to visit their SOC.) See the seminar agenda and detailed information in the attached report. - Project Filming by APNIC Foundation
On February 29, 2024, a filming crew from Fade In Pro came to our office to shoot the interview about this project for the APNIC Foundation. - SOC Workshop
After the seminar, several security providers contact us to learn more about how to utilize our open-source SOC in their business. Since the software is all open-source, there is no licensing fee involved. In order to get these companies started, we organized a free workshop to teach them the installation, configuration, and operation process of our SOC software. The workshop was on April 29, 2024 at NECTEC NSTDA, Pathumthani, Thailand with 18 participants from 6 companies.
Impact story
After three months of field testing, we conducted interviews with three pilot factories to gather their feedback on our Security Operations Center (SOC) service. The feedback was collected from both the factory owners and their IT staff to provide a comprehensive perspective.
Awareness and understanding.
Q1. How does our SOC service enhance their security awareness and understanding?
Before initiating this project, our investigation revealed that none of the three pilot factories had any direct interactions or experiences with SOC services. This project offered them an opportunity to develop a deeper understanding of cybersecurity and the functionalities of a SOC. According to our interviews, which focused on network architecture and security with their IT staff, we initially found a lack of awareness regarding cybersecurity issues. Moreover, they expressed concerns about the security vulnerabilities associated with using open-source remote access software such as "AnyDesk," which highlighted issues related to the availability and remote accessibility of their network. After utilizing our SOC service, they recognized these vulnerability issues and increased their awareness of the risks associated with such remote desktop software. This awareness has resulted in a limitation of using such software in the critical infrastructure of their network.
Perceived importance
Q2. How important do they believe having a SOC is for an organization’s overall cybersecurity strategy?
Initially, two of the factories mentioned that they did not fully understand what exactly a SOC service entailed. They believed that such a service was unnecessary for their operations due to the small scale of their networks. However, after receiving monthly reports for three months, they recognized how a SOC can effectively visualize and monitor their network security. This realization significantly increased their perceived need for a SOC service in their facilities.
Usage and Integration
Q3. Do these pilot factories currently utilize a Security Operations Center (SOC)?
None of the pilot factories utilize an in-house SOC or an outsourced SOC service. Some have implemented security appliances within their networks to guard against malicious attacks. Traditionally, the security monitoring tasks were manually performed by IT staff, who checked configuration rules and reviewed firewall and server logs. This process was cumbersome, and real-time vulnerability checks were not feasible. After joining this project and integrating our SOC service into their networks, we provided 24/7 security monitoring, enabling nearly real-time vulnerability alerts through SOC analysts and Line chat.
Performance and Satisfaction
Q4. How satisfied are they with the performance of our SOC in terms of responding to and mitigating security threats?
Overall, most of the pilot factories are satisfied with our SOC service, particularly regarding its visibility and monitoring capabilities. Once incidents occur, SOC analysts notified the IT staff at the factories responsible for incident response almost immediately. The IT staff received alerts along with recommendations on how to mitigate the issues. However, the IT staff would like to have more detailed guidance on how to mitigate threats, along with a comprehensive playbook for security response and recovery.
Impact and Outcomes
Q5: How do they believe a SOC contributes to the overall resilience of their organizations against cyber threats?
We explored the impact of integrating SOC services within IT/OT networks to enhance resilience against cyber threats. Although the findings are not statistically significant due to the short-term nature of the pilot implementation, we observed noticeable improvements in network configuration and security awareness among participants, particularly in recognizing misconfigurations and misuse of security and software tools. These enhancements have contributed to the overall resilience of their organizations against cyber threats.
Future Prospects
Q6. What additional features or capabilities would you like to see in future developments of SOCs?
Most of the factories expressed a desire for additional services to be integrated with our SOC offerings, such as vulnerability scanning, asset inventory, and a network architecture review prior to the installation of monitoring tools for the SOC service. Furthermore, there is a strong interest in recommendation on incident response and recovery processes to enhance efficiency and effectiveness.
Project Sustainability
Because this project is open-source, we plan to maintain the software on github. In terms of service, however, we, as a government organization, cannot provide 24/7 monitoring service. We plan to hand it to security providers to adopt this software and offer commercial SOC services. In order to do that, there is a barrier in learning and training of open-source software. That is why we decided to add a free workshop to train service providers how to install, configure, operate, and modify this set of open-source software. After this free workshop, any service providers who wish to use this software can ask for additional training and consultation from us for a fee.
This project creates new opportunities such as
1) We and NCSA co-wrote a proposal for funding to educate a larger group of service providers on this open-source SOC.
2) True Digital Group sponsored the seminar event on February 5, 2024.
3) Internet Thailand PCL consulted us on how to apply artificial intelligence to learn new attack behaviors on their data center service.
Some of the training and consulting activities will continue after the end of the grant through NECTEC and SMC's support. We hope to develop a proposal for ISIF or other funding sources to enhance the SOC service through AI capabilities, for example.
Project Management
Project management proceeded smoothly, with a positive change to the original plan. We recruited a new member to our project team, eliminating the need to hire consultants for designing and maintaining the service. Consequently, we reallocated that budget toward purchasing equipment for installation in factories. However, during the evaluation process, we experienced a slight delay in selecting pilot factories and completing necessary documents, such as non-disclosure and collaboration agreements. As a result, the project timeline was extended by three months.
Overall, the project went according to plan. Some initial findings indicate that convincing factories of the necessity for cybersecurity protection for their OT infrastructure is very challenging. Many factories refused our invitation to test our SOC platform, fearing that our program would access their sensitive manufacturing data or disrupt normal operations. Despite this, we managed to recruit three factories willing to participate in the pilot test, although they were somewhat hesitant. We are grateful for their cooperation. However, we faced some difficulties. For instance, when a factory's Wi-Fi stopped working, they asked us to disable our agents, readily believing that our system was the cause, even though it was unrelated. This incident highlighted the challenge of scaling up our SOC-as-a-service platform to more factories, given the low cybersecurity awareness and understanding among SME factories.
After completing the pilot test, we organized a one-day seminar targeting factories and automation system integrators. The seminar was very well received, as it was a rare event focusing on OT security awareness. It brought together IT/security professionals and manufacturing professionals. During the seminar, our team gained first-hand experience inside a commercial SOC and learned about building SOCs from a large bank. We realized that our open-source SOC developed in this project is still far from commercial standards. One significant lacking feature is threat intelligence, which is crucial for a SOC service. The open-source threat intelligence we use is sufficient but inadequate for combating zero-day attacks.
Our seminar was honored to host the director of Thailand’s NCSA (National Cyber Security Agency). This event resulted in a close relationship between our organization and the NCSA. An MOU was signed between NSTDA and NCSA, and we collaborated on writing a project proposal to disseminate the open-source SOC for nationwide utilization.
Project Recommendations and Use of Findings
We have tested our prototype open-source SOC-as-a-service with three factories in Thailand since September 2023. These factories manufacture a range of products, including herbal supplements, plastic bottles, and vegetable oil. Two of them are SMEs, and one is a large enterprise. We have discovered incidents that led to alerts and responses, such as suspicious DNS queries, which turned out to be malware attempting to connect to a cryptocurrency server. Another suspicious incident involved the use of remote services like AnyDesk and TeamViewer. However, these were legitimate connections, as these services are commonly used in Thai enterprises.
We find it challenging to determine whether incidents are actual security threats, especially in small to medium-sized organizations, as they often lack proper security policies. Consequently, many apparent security incidents are merely non-malicious activities that do not follow good security practices. We will continue validating and developing our service and hope to expand it to serve more factories in the future.
This project achieves the goal of choosing and integrating open-source software tools to create a security operation center service. The prototype open-source SOC service was field tested with three factories for at least three months. The results and user feedback show that it is effective to use with small and medium sized factories, and it can stimulate cybersecurity awareness in factories. We communicated our results and best practices through seminars, presentations, and workshops. In order to bring our SOC tool to real use, we realize that we need system integrators / security providers to transfer the technology from our lab to real commercial services. There were 6 security providers that expressed interest in technology transfer. So we organized a workshop to teach them how to install, configure, and integrate these software tools. We will follow up with them after the project completion to assist them in implementing the open-source SOC services for their customers.
Bibliography
[1] S. Kowtha, L. A. Nolan and R. A. Daley, "Cyber security operations center characterization model and analysis," 2012 IEEE Conference on Technologies for Homeland Security (HST), Waltham, MA, USA, 2012, pp. 470-475, doi: 10.1109/THS.2012.6459894.
[2] M. Vielberth, F. Böhm, I. Fichtinger and G. Pernul, "Security Operations Center: A Systematic Study and Open Challenges," in IEEE Access, vol. 8, pp. 227756-227779, 2020, doi: 10.1109/ACCESS.2020.3045514.
[3] N. Miloslavskaya, "Security Operations Centers for Information Security Incident Management," 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria, 2016, pp. 131-136, doi: 10.1109/FiCloud.2016.26.
[4] A. Perera, S. Rathnayaka, N. D. Perera, W. W. Madushanka and A. N. Senarathne, "The Next Gen Security Operation Center," 2021 6th International Conference for Convergence in Technology (I2CT), Maharashtra, India, 2021, pp. 1-9, doi: 10.1109/I2CT51068.2021.9418136.
[5] F. Ahmed, U. Jahangir, H. Rahim, K. Ali and D. -e. -S. Agha, "Centralized Log Management Using Elasticsearch, Logstash and Kibana," 2020 International Conference on Information Science and Communication Technology (ICISCT), Karachi, Pakistan, 2020, pp. 1-7, doi: 10.1109/ICISCT49550.2020.9080053.
[6] V. D. Kumar, R. R. Shah and A. Philip, "Centralized log management for pepper," 2011 IEEE Third International Conference on Cloud Computing Technology and Science, Athens, Greece, 2011, pp. 1-3, doi: 10.1109/CloudCom.2011.128.
[7] Fluentd. "Output plugin overview." Fluentd documentation. [Online]. Available: https://docs.fluentd.org/output. [Accessed: Feb 22, 2023].
[8] Fluent Bit. "Fluentd and Fluent Bit." [Online]. Available: https://docs.fluentbit.io/manual/about/fluentd-and-fluent-bit. [Accessed: Jun 1, 2023].
[9] Graylog. "Planning Your Deployment." [Online]. Available: https://go2docs.graylog.org/5-0/planning_your_deployment/planning_your_deployment.html. [Accessed: Feb. 19, 2023].
[10] Apache Kafka. "Documentation." Apache Kafka, 2019. [Online]. Available: https://kafka.apache.org/documentation/. [Accessed: Feb 20, 2023].
[11] IBM Cloud Architecture. (n.d.). Kafka Overview. Retrieved February 23, 2023, from https://ibm-cloud-architecture.github.io/refarch-eda/technology/kafka-overview/
[12] Cloudera, Inc. "Apache Kafka - Overview." Hortonworks Data Platform, version 2.6.1. [Online]. Available: https://docs.cloudera.com/HDPDocuments/HDP2/HDP-2.6.1/bk_kafka-component-guide/content/ch_overview_kafka.html. [Accessed: Feb 20, 2023].
[13] R. Singh, "Getting Started with rsyslog in Linux," GeeksforGeeks, 17 March 2021. [Online]. Available: https://www.geeksforgeeks.org/getting-started-with-rsyslog-in-linux/. [Accessed: 22 February 2023].
[14] Rainer Gerhards. (2021). rsyslog Architecture [Image], Available: https://www.rsyslog.com/. [Accessed: Feb 19, 2023].
[15] J. Partain, "Rsyslog Plugin Overview," [Online]. Available: https://www.rsyslog.com/plugin-overview/. [Accessed: Feb 20, 2023].
[16] Elastic Stack, “Welcome to Elastic Docs”, [Online]. Available: https://www.elastic.co/elastic-stack/. [Accessed: Feb. 28, 2023].
[17] M. A. Fathahillah, "An Overview on Elasticsearch and its Usage," Towards Data Science, 12 September 2021. [Online]. Available: https://towardsdatascience.com/an-overview-on-elasticsearch-and-its-usage-e26df1d1d24a. [Accessed: Feb 20, 2023].
[18] A. Verma, "ELK (Elasticsearch, Logstash, Kibana) Conceptual Tutorial for Beginners," Medium, 19 October 2020. [Online]. Available: https://faun.pub/elk-elasticsearch-logstash-kibana-conceptual-tutorial-for-beginners-2a7a827305b8. [Accessed: Feb 19, 2023].
[19] DBI services. "Elastic (ELK) Stack: Elasticsearch Terminologies". dbi services Blog, 15 June 2018. [Online]. Available: https://www.dbi-services.com/blog/elastic-elk-stack-elasticsearch-terminologies/. [Accessed: Feb 18, 2023].
[20] Elastic Beats, [Online]. Available: https://www.objectrocket.com/resource/what-are-elasticsearch-beats/. [Accessed: Feb 27, 2023]
[21] Elastic Logstash, [Online]. Available: https://www.elastic.co/logstash/. [Accessed: Feb 27, 2023]
[22] Elastic. (n.d.). Beats reference. Retrieved February 24, 2023, from https://www.elastic.co/guide/en/beats/libbeat/current/beats-reference.html
[23] M. Amer, "Logstash for Synchronize Elasticsearch with DBs," Medium, 28 June 2020. [Online]. Available: https://mohaamer5.medium.com/logstash-for-synchronize-elasticsearch-with-dbs-e5dda7cea930. [Accessed: 20 February 2023].
[24] Kibana, [Online]. Available: https://www.elastic.co/kibana/. [Accessed: Mar 1, 2023]
[25] Threat Intelligence Platform, [Online]. Available: https://en.wikipedia.org/wiki/Threat_Intelligence_Platform. [Accessed: Mar 4, 2023]
[26] Tim Wilson, “Threat Intelligence Platform: The Next Must-Have for Harried Security Operations Teams, Jun 2015. [Online]. Available: https://www.darkreading.com/attacks-breaches/threat-intelligence-platforms-the-next-must-have-for-harried-security-operations-teams. [Accessed: Mar 04, 2023].
[27] M. Senftleben and A. Willemsen, "Introduction to Information Sharing with MISP," MISP Project, [Online]. Available: https://www.misp-project.org/documentation. [Accessed: Mar 18, 2023].
[28] S. Zeb, M. Shahid, R. Ahmad, N. Javaid, "MISP vs. OpenCTI: A Comparative Study of Cyber Threat Intelligence Sharing and Analysis Platforms," Computers & Security, vol. 110, p. 102310, Jan. 2022.
[29] CIRCL (Computer Incident Response Center Luxembourg). (n.d.). MISP - Malware Information Sharing Platform & Threat Sharing. In MISP (Malware Information Sharing Platform) User Guide (p. 64), [Online]. Available: https://www.circl.lu/doc/misp/book.pdf. [Accessed: Mar 19, 2023].
[30] A. Al Jallad, I. Aloulou, and M. Samet, "A Comparative Study of OpenCTI and MISP for Cyber Threat Intelligence Sharing and Analysis," Journal of Cybersecurity and Privacy, vol. 1, no. 1, pp. 1-16, Dec. 2021.
[31] Filigran. (n.d.). Open CTI Architecture. [Online]. Available: https://filigran.notion.site/Architecture-5ce8241eac7e4e24906249e9595314cd [Accessed: Mar 20, 2023].
[32] ANSSI, “OpenCTI – The Open Source Solution for Processing and Sharing Threat intelligence Knowledge”, [Online]. Available: https://www.ssi.gouv.fr/actualite/opencti-the-open-source-solution-for-processing-and-sharing-threat-intelligence-knowledge/ [Accessed: Apr 7, 2023].
[33] MITRE ATT&CK. [Online]. Available: https://attack.mitre.org/ [Accessed: Apr 7, 2023].
[34] Structured Threat Information Expression (STIX). [Online]. Available: https://oasis-open.github.io/cti-documentation/ [Accessed: Apr 7, 2023].
[35] GraphQL, “A Query Language for your API”. [Online]. Available: https://graphql.org/ [Accessed: Apr 5, 2023].
[36] TheHive. [Online]. Available: https://github.com/TheHive-Project/TheHive [Accessed: Apr 5, 2023].
[37] MISP, “Threat Intelligence Sharing Platform”. [Online]. Available: https://github.com/MISP/MISP [Accessed: Apr 5, 2023].
[38] Alves, M. M. (2021). OpenCTI as Threat Intelligence Platform for Security Operation Centers. In Proceedings of the 16th International Conference on Evaluation of Novel Approaches to Software Engineering (pp. 679-686).
[39] Filigran. (n.d.). OpenCTI. Data visualization is a feature of OpenCTI, a cyber threat intelligence platform offered by Filigran. [Online]. Available: https://www.filigran.io/en/products/opencti/. [Accessed: Mar 19, 2023].
[40] CRITs. (n.d.). What Is CRITs? . [Online]. Available: https://github.com/crits/crits. [Accessed: Mar 21, 2023].
[41] Schrottner, J., et al. (2021). The Landscape of Cyber Threat Intelligence Platforms: An Evaluation Framework for Researchers and Practitioners. 10th International Conference on Decision Support System Technology, ICDSST 2021. [Online]. Available: https://diglib.uibk.ac.at/ulbtirolhs/download/pdf/6676638?originalFilename=true. [Accessed: Mar 19, 2023].
[42] CRITs. [Online]. Available: https://crits.github.io/ [Accessed: Apr 7, 2023].
[43] Cheng, F., Li, W., Li, W., Li, Y., Li, H., & Li, Y. (2021). A Risk Management System for Hotels Based on Threat Intelligence. Journal of Ambient Intelligence and Humanized Computing, 11(12), 5521-5532.
[44] Center for Internet Security. (2021). Collective Intelligence Framework (CIF). [Online]. Available: https://csirtgadgets.com/collective-intelligence-framework/ [Accessed: Mar 22, 2023].
[45] Greg Farnham, “Tools and Standards for Cyber Threat Intelligence Projects”, Jun 2012. Online]. Available: https://www.giac.org/paper/gcpm/134/tools-standards-cyber-threat-intelligence-projects/108367 [Accessed: Apr 10, 2023].
[46] Extensible Markup Language (XML). [Online]. Available: https://www.w3.org/XML/ [Accessed: Apr 7, 2023].
[47] JSON. [Online]. Available: https://www.json.org/json-en.html [Accessed: Apr 7, 2023].
[48] CSV – Common Separated Values. [Online]. Available: https://datahub.io/docs/data-packages/csv [Accessed: Apr 7, 2023].
[49] Melo e Silva, A. de, Gondim, J.J.C., Oliveira Albuquerque, R. de, Villalba, L.J.G.: A Methodology to Evaluate Standards and Platforms within Cyber Threat Intelligence. Future Internet, 1-23 (2020)
[50] Tounsi, W., Rais, H.: A survey on technical threat intelligence in the age of sophisticated cyber attacks. In: Computers & Security 72, 212-233 (2018)
[51] Staiger, T. (2021). Cyber Threat Intelligence Sharing Platforms: A Comprehensive Analysis of Software Vendors and Research Perspectives. Master's thesis, University of Innsbruck.
[52] Lodi, M. (2023). IntelOwl. [Online]. Available: https://intelowl.readthedocs.io/ [Accessed: Mar 20, 2023].
[53] Intel Owl. (2021, September 13). Intel Owl Release v3.0.0. The Honeynet Project. [Online]. Available: https://www.honeynet.org/2021/09/13/intel-owl-release-v3-0-0/. [Accessed: Mar 21, 2023]
[54] F. Sabahi and A. Movaghar, "Intrusion Detection: A Survey," 2008 Third International Conference on Systems and Networks Communications, Sliema, Malta, 2008, pp. 23-26, doi: 10.1109/ICSNC.2008.44.
[55] Palo Alto Networks, “What is an Intrusion Detection System?”, Mar 2022. [Online]. Available: https://www.paloaltonetworks.com/cyberpedia/what-is-an-intrusion-detection-system-ids [Accessed: May 15, 2023].
[56] Waleed, A., Jamali, A. F., & Masood, A. (2022). Which open-source IDS? Snort, Suricata or Zeek. Computer Networks, 213, 109116.
[57] The Snort Project. (2020, April 8). Snort Users Manual (Version 2.9.16). [Online]. Available: https://snortorgite.s3.amazonaws.com/production/document_files/files/000/000/249/original/snort_manual.pdf. [Accessed: Mar 29, 2023].
[58] Gavrilović, N., Ćirić, V., & Lozo, N. (2022). Snort IDS System Visualization Interface for Alert Analysis. Serbian Journal of Electrical Engineering, 19(1), 67-78. DOI: https://doi.org/10.2298/SJEE2201067G.
[59] Shuai, L., & Li, S. (2021). Performance optimization of Snort based on DPDK and Hyperscan. Procedia Computer Science, 183, 837-843. doi: 10.1016/j.procs.2021.02.172
[60] Abdulrezzak, S., & Sabir, F. A. (2023). Enhancing Intrusion Prevention in Snort System. In Proceedings of the 2023 15th International Conference on Developments in eSystems Engineering (DeSE) (pp. 1-5). IEEE. DOI: 10.1109/DESE58274.2023.10099757
[61] OISF, "Suricata User Guide Release 5.0.3." [Online]. Available: https://suricata.readthedocs.io/_/downloads/en/suricata-5.0.3/pdf/. [Accessed: April 7, 2023].
[62] I. Ghafir, V. Prenosil, J. Svoboda, & M. Hammoudeh, “A survey on network security monitoring systems,” 2016 IEEE 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW).
[63] Fekolkin, R. (2015). Intrusion Detection and Prevention Systems: Overview of Snort and Suricata. Internet Security, A7011N. Luleå University of Technology.
[64] Alves, A. F. P. (2020). Integrating an Intrusion Detection System with Heterogeneous IoT Endpoint Devices (Thesis). Universidade do Minho, Escola de Engenharia. Retrieved from. DOI: 10.13140/RG.2.2.21711.92328.
[65] Fadhilah, D., & Marzuki, M. I. (2020). Performance Analysis of IDS Snort and IDS Suricata with Many-Core Processor in Virtual Machines Against DoS/DDoS Attacks. In Authorized licensed use limited to: National Science & Technology Development Agency. In 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT) (pp. 78-1-7281-7450).
[66] Hua, Q., Yu, S.-Y., & Asghar, M. R. (2020). Analysing performance issues of open-source intrusion detection systems in high-speed networks. Journal of Information Security and Applications, 51, 102426. DOI: 10.1016/j.jisa.2019.102426
[67] Zeek, 2022. “The zeek network security monitor”. [Online]. Available: https://zeek.org/. [Accessed: April 25, 2023].
[68] The Cyber Center for Security and Analytics. (2020). Zeek Intrusion Detection Series: Lab 1 - Introduction to the Capabilities of Zeek. Document Version: 03-13-2020.
[69] Muhammad, A.R., Sukarno, P., Wardana, A.A. (2023). Integrated Security Information and Event Management (SIEM) with Intrusion Detection System (IDS) for Live Analysis based on Machine Learning. Procedia Computer Science, 217, 1406-1415.
[70] Elvira Nassirova, “Data Visualization Dashboard: Benefits, Types, and Examples”, Jan 2023. [Online]. Available: https://blog.coupler.io/what-is-data-visualization-dashboard/ [Accessed: May 18, 2023].
[71] Sameer Bhale, “Dashboard Data Visualization: Benefits, Types, and Examples”, Feb 2023. [Online]. Available: https://www.knowledgehut.com/blog/business-intelligence-and-visualization/dashboard-data-visualization [Accessed: May 18, 2023].
[72] Apache Superset. (2021). Introduction to Apache Superset - Apache Superset documentation. [Online]. Available: https://superset.apache.org/docs/intro/. [Accessed: Mar 21, 2023].
[73] Grafana. (n.d.). Dashboards. Retrieved March 29, 2023, [Online]. Available: https://grafana.com/docs/grafana/latest/dashboards/ [Accessed: Mar 21, 2023].
[74] Grafana documentation. (n.d.). Demo Dashboards. [Online]. Available: https://play.grafana.org/d/000000012/grafana-play-home?orgId=1. [Accessed: Mar 21, 2023].
[75] Leppänen, T. (2021). Implementation of Grafana monitoring tool for containerized microservices (Bachelor's thesis, Turku University of Applied Sciences). [Online]. Available: https://www.theseus.fi/bitstream/handle/10024/512860/Turkuamk_Bachelors_Thesis_Leppanen_Tiia.pdf?sequence=2&isAllowed=y . [Accessed: Mar 21, 2023].
[76] Metabase. (n.d.). Tour of Metabase. Retrieved from https://www.metabase.com/learn/getting-started/tour-of-metabase#how-to-query-and-visualize-your-data
[77] Elasticsearch BV. (2021). Kibana: Introduction. [Online]. Available: https://www.elastic.co/guide/en/kibana/current/introduction.html. [Accessed: Mar 24, 2023].
[78] OpenSearch contributors. (2023). Introduction to OpenSearch [Documentation]. Retrieved from https://opensearch.org/docs/latest/. [Accessed: Jun 1, 2023].
[79] Opster Expert Team - Gustavo. "OpenSearch Observability Visualizations: How to Use Notebooks and Operational Panels." [Online]. Available: https://opster.com/guides/opensearch/opensearch-basics/opensearch-dashboards-visualizations-notebooks-operational/. Updated: Oct 30, 2022. [Accessed: June 1, 2023].
This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 


