TECHNICAL REPORT
| Grantee |
Swiss German University (SGU), Indonesia Honeynet Project (IHP) and Asosiasi Penyelenggara Jasa Internet Indonesia (APJII)
|
| Project Title | HoneyV6 ID - Implementing the next generation honeypot to support IPv6 at ISPs and IXPs |
| Amount Awarded | USD 85,000 |
| Dates covered by this report: | 2023-10-01 to 2024-12-16 |
| Economies where project was implemented | Indonesia |
| Project leader name |
Kalpin Erlangga.S
Charles Lim
|
| Project Team |
Eka Budiarto
Siti Ayu Diana Lestari
Yevonnael Andrew
Arry Abdi Syalman
Kevin Hobert
|
Project Summary
Cyber-attacks are increasing in Indonesia, particularly targeting organizations with ransomware and malware. To address this, a joint research project involving the Indonesia Honeynet Project community, Swiss German University (SGU) academics, and the Indonesia Internet Service Provider Association was formed. The project aims to evaluate the effectiveness of deploying honeypots at Internet Exchange Points (IXPs) and Internet Service Providers (ISPs) to enhance security and reduce attacks. The research will deploy honeypots at various IXP and ISP locations, gathering data on threats in both IPv4 and IPv6 networks.
HoneyV6 ID represented the most recent phase in this project.
This project aims to compare threat attacks in IPv4 and IPv6 networks, providing statistics on the types and frequencies of these attacks. It emphasizes the importance of the findings for improving network security and recommends implementing honeypots in IXPs and ISPs for better threat detection and prevention. The collaboration between academia, community, and industry is expected to contribute both to theoretical knowledge and practical network security applications in Indonesia.
The project highlights the significance of security in IPv4 and IPv6 networks, outlines objectives such as deploying honeypots, collecting and analyzing threat data, and comparing results between IPv4 and IPv6. It also details the methodology for implementing honeypots, data collection, and analysis.

Table of Contents
- Background and Justification
- Project Implementation Narrative
- Project Activities, Deliverables and Indicators
- Project Review and Assessment
- Diversity and Inclusion
- Project Communication
- Project Sustainability
- Project Management
- Project Recommendations and Use of Findings
- Bibliography
Background and Justification
Cyber-attacks have been increasingly targeting organizations in Indonesia, primarily through ransomware and malware. This escalating threat necessitates more proactive and effective measures to safeguard the country's digital infrastructure. Previously, the predominant approach to cybersecurity has been reactive, addressing attacks after they occur rather than preventing them. Recognizing the limitations of this method, a joint research project has been initiated by the Indonesia Honeynet Project community, Swiss German University (SGU) academics, and the Indonesia Internet Service Provider Association. This project aims to investigate the implementation of honeypots in Internet Exchange Points (IXPs) and Internet Service Providers (ISPs) as a proactive solution to enhance infrastructure security and mitigate cyber-attacks.
The problem this project seeks to solve is the growing incidence of cyber-attacks on Indonesian organizations, which current reactive measures fail to adequately prevent. Previous attempts to tackle this issue have largely focused on post-attack mitigation rather than prevention, highlighting a gap in proactive security strategies. The motivation for this project stems from the urgent need to shift towards a more anticipatory approach in cybersecurity, using honeypots to detect and prevent attacks before they cause significant damage.
The research plan involves deploying honeypots at various IXP and ISP locations to collect comprehensive data on threat attacks, with a particular focus on comparing their occurrence in both IPv4 and IPv6 networks. This will enable a thorough analysis of the types and frequencies of attacks in different network environments. The expected outcomes include a detailed comparison of threat attacks across these networks and the development of statistics that highlight the most common and dangerous threats. Additionally, the methodology has been refined to ensure more precise data collection and analysis processes, enhancing the overall accuracy and relevance of the research findings.
Overall, this joint research project holds significant potential for improving infrastructure security in Indonesia by providing actionable insights into the effectiveness of honeypots in detecting and preventing cyber threats in both IPv4 and IPv6. By addressing the limitations of reactive cybersecurity measures, this project aims to contribute valuable theoretical knowledge and practical applications that can enhance the security of networks both in Indonesia and globally.
Project Implementation Narrative
The project has been successfully completed, with honeypot sensors now deployed at eight Indonesia Internet Exchange (IIX) locations: Batam, Lampung, Jakarta, Bandung, Surabaya, Bali, and Makassar. While the original plan included seven locations, APJII later requested an additional deployment in Bali to capture a higher volume of attack data from this region. A public dashboard, accessible at https://monitoring.apjii.or.id, has been developed by APJII to serve as a valuable reference for its members, primarily Internet Service Providers across Indonesia. Looking ahead, we aim to enhance the dashboard with advanced features and insights to better address the diverse needs of APJII members.
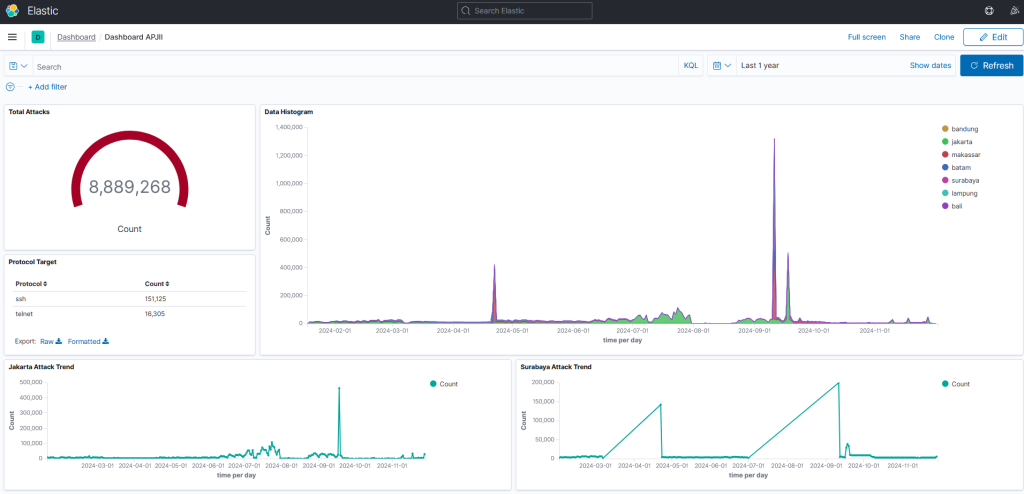
During the implementation phase, we faced several challenges related to installing and configuring the honeypot and its components, such as Docker, directly from source code. A key issue was that the honeypot within the IIX network lacked access to the Internet to retrieve necessary packages and software. To address this, we attempted to use a forward proxy by configuring Squid on a server with dual interfaces—one connected to the IIX infrastructure and the other to the Internet. However, some dependency packages remained inaccessible due to additional customization requirements, such as configuring Docker to work with the proxy and support IPv6. Another challenge arose whenever customization of the honeypot was needed, as it required downloading packages from the Internet. To overcome this, we established a dedicated repository within the IIX infrastructure to store the Dockerized honeypot and its components. This solution has significantly streamlined the process, enabling smooth deployment and rebuilding of honeypots across other IIX locations.
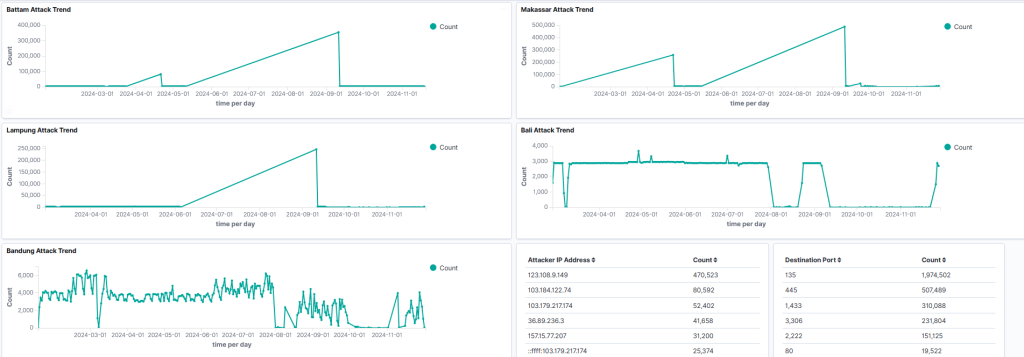
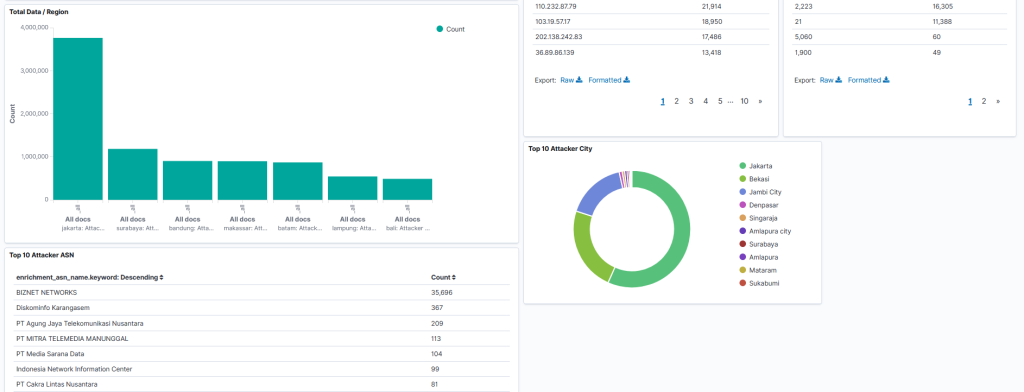
The deployment of honeypots at IIX locations has yielded significant insights. For example, APJII has collected data from various sites showing that attacks begin almost immediately after honeypot activation, with numerous attempts to brute-force authentication systems to gain unauthorized access. The data also reveals that while attacks on IPv6 are less frequent compared to IPv4, they are still present, indicating that attackers predominantly target IPv4 networks. Additionally, the honeypot findings have helped identify the types of services most commonly targeted by attackers, enabling APJII to offer tailored security recommendations to its members. With the implementation phase now complete, we anticipate the honeypot data will continue to grow, serving as a valuable resource for future research and strengthening the cybersecurity posture of APJII members.
This project would not have been possible without the invaluable support of research assistants. The project team comprised students from Swiss German University (SGU) and engineers from APJII. Many of the SGU researchers used this initiative as the foundation for their thesis work. Through their involvement, these students not only gained hands-on experience managing tasks but also honed their teamwork and project management skills. SGU benefits from this collaboration by providing students with the opportunity to work on a real-world project, enriching their academic and professional development. APJII also gains significant advantages, as the honeypot data helps them refine their security policies and implement measures to mitigate potential risks. Furthermore, the Indonesia Honeynet Project (IHP) community benefits from the collaboration, with members contributing to the analysis of honeypot data to extract valuable insights into the security impact of its implementation, particularly within the IIX infrastructure.
A research paper exploring the use of an MSSQL honeypot to enhance cybersecurity has been presented and is set to be indexed by IEEE. Similarly, two other papers—one focusing on Redis honeypots and the other on the Snare Tanner honeypot for dynamic web applications—have been accepted and recently presented. All these studies gratefully acknowledge the research funding and support provided by the APNIC Foundation via ISIF Asia.
Project Activities, Deliverables and Indicators
Activities
| Activity | Description | #Months |
|---|---|---|
| Honeypot Research | Researching new honeypot types that can be used in both IPv4 and IPv6 network that most relevant with current security threats in Indonesia. | 3 |
| Data Collection Study | Researching framework that can be used to collect huge data from various locations. | 3 |
| Threat Correlation and analysis | Researching methods to correlate data honeypot from various honeypot types and locations. Researching for data analysis specifically data that collected from IXPs and ISPs. | 4 |
| New Server | Procuring, preparing and configuring new server that can be used to handle huge data processing using various AI algorithms | 6 |
Middle of Project
| Activity | Description | #Months |
|---|---|---|
| Data Visualization | Researching for data visualization to find the best way to visualize data in a dashboard to ease data analysis. | 4 |
| Survey Environment | Conduct a survey to the location of IXPs and ISPs where the honeypot will be installed later. | 6 |
| System Development & Testing | Developing a system to support sending data from various IXPs and ISPs locations to a repository, analyzing threat patterns and categorizing threat patterns and visualizing threat into the dashboard. | 6 |
| Honeypot Deployment | Deploying honeypots at various IXPs and ISP locations | 6 |
End of Project
| Activity | Description | #Months |
|---|---|---|
| Paper Publication | Research and summarize all relevant works and research results into relevant paper format for publication | 3 |
| Reporting | Documenting all relevant results for ISIF report | 3 |
Throughout the Project
| Activity | Description | #Months |
|---|---|---|
| Literature Study | Researching recent publications about approach for honeypot implementation in both IPv4 and IPv6 specifically in IXPs and ISPs. | 12 |
Project Review and Assessment
At the outset, our research assistants had limited practical experience with deploying honeypots and analyzing cyberattacks. However, through active participation in this project, they have gained the skills to effectively deploy honeypots, collect and analyze data, and share their findings through academic publications. The project has enabled them to deepen their knowledge and sharpen their skills by immersing themselves in data analysis and studying the behaviors of threats and attackers. These experiences have helped them cultivate a well-rounded balance between academic expertise and practical proficiency.
Diversity and Inclusion
Our project proposal included specific elements addressing gender equality and social inclusion. During this reporting period, we have made several improvements in these areas, benefiting both our internal team and the external community served.
- The project actively engaged women, with two women participating as part of our project team. Their contributions have been vital in various aspects of the project, from planning to execution.
- Externally, our workshops and seminars welcomed participants of all genders, ensuring inclusive access to knowledge and resources.
- Gender equality and inclusion were addressed by incorporating diverse perspectives in decision-making processes. The team maintained a collaborative environment where all members, regardless of gender, had equal opportunities to contribute and lead.
- Our team includes an expert advisor who has a disability, highlighting our commitment to inclusivity. Their expertise has been invaluable, and their active participation underscores the project's support for people with disabilities.
- Externally, our hybrid workshops (online and onsite) ensured accessibility for participants with disabilities, promoting an inclusive learning environment.
- The team comprises members from various religious, cultural, and geographical backgrounds. We use Bahasa Indonesia for communication, accommodating members from different linguistic backgrounds while fostering a cohesive team dynamic.
- Our collaboration with SGU and APJII has been instrumental in promoting diversity and inclusion. The joint workshops and seminars have been open to all, addressing critical issues like website defacement, particularly targeting government and educational websites in Indonesia (.ID TLD). One key topic was the use of honeypots to detect and mitigate such attacks. The inclusive nature of our seminars, addressing pressing issues like website defacement and online gambling, attracted participants from diverse cultural backgrounds, contributing to broader community engagement.
- While we did not specifically inquire about the backgrounds of our team members, our focus remained on fostering collaboration to build a secure internet environment, especially within the IIX infrastructure using honeypots.
By prioritizing diversity and inclusion, our project not only achieved its technical goals but also contributed to a more equitable and inclusive community.
Project Communication
1) Communication and Dissemination Efforts:
- Internal Communication: We held weekly meetings for the internal team to update on project progress and address any issues. Specific tasks were also discussed in separate weekly technical meetings to ensure detailed attention to technical aspects.
- Project Tracking: We utilized Asana, a project collaboration tool, to track our progress and generate reports. This tool has been instrumental in maintaining transparency and accountability within the team.
- Reporting to APJII: Regular progress reports on installation and configuration were submitted to APJII, which manages the IIX infrastructure. This ensured that they were kept informed and could provide necessary support.
- Public Data Sharing: Honeypot data is made openly available on APJII servers, allowing internal use and sharing with APJII members (ISPs). We also shared attack statistics on our public dashboard, making it accessible to anyone interested.
- External Collaboration: We are open to collaborating with other organizations, provided we have consent and filter sensitive information such as honeypot IPs. This openness fosters broader engagement and information sharing.
2) Community Engagement:
- Beneficiary Engagement: The community of beneficiaries, including ISPs and other stakeholders, was actively engaged through the public dashboard and regular updates from APJII. This ensured that they were aware of the project's progress and could leverage the findings for their own security measures.
- Workshops and Seminars: We organized workshops and seminars in collaboration with SGU and APJII, open to all, to disseminate knowledge and promote project activities. These sessions covered critical issues like website defacement and ransomware, enhancing community awareness and participation.

3) Sharing Findings and Lessons Learned:
- Information Sharing: Our findings and lessons learned were shared with other organizations, particularly during incidents or issues in Indonesia. For example, we shared insights when the Temporary National Datacenter was infected by ransomware and during web defacement incidents involving online gambling.
- Utilization of Shared Information: Other organizations have used the shared information to improve their own security measures and response strategies, benefiting from our research and practical experiences.
4) Networking and Participation in Events:
Incident Response Collaboration: Invitations from other organizations to share our research during incidents highlighted our role as a key contributor to the broader security community in Indonesia.
Project Sustainability
The project has been successfully completed, and we are now planning to gather feedback to identify ways to deliver even better insights in future projects. To sustain and expand its scope, we aim to seek additional funding from organizations such as DIKTI, a subsidiary of the Ministry of Education that supports research initiatives.
Project Recommendations and Use of Findings
The HoneyV6 ID project has yielded valuable insights into the implementation and effectiveness of honeypots in monitoring and mitigating cyber threats at Internet Exchange Points (IXPs). Throughout the project's duration, findings and lessons learned have significantly shaped decision-making, guiding adjustments in deployment strategies and technical configurations. One of the key insights was the importance of maintaining data integrity during log transfers, leading to the adoption of Fluentd for raw data collection. Additionally, the need to overcome connectivity issues within the isolated IIX network drove the development of innovative solutions, such as the local Docker registry and the proxy VM, which streamlined the deployment and maintenance of honeypots across multiple locations.
These lessons have been shared with other organizations, particularly through APJII's public dashboard, which provides real-time data on network attacks. By making this data accessible to Internet Service Providers (ISPs) across Indonesia, the project has encouraged a more proactive approach to network security. APJII has utilized these findings to enhance their security policies, advising ISPs on how to better safeguard their infrastructure based on the trends observed from honeypot data. Furthermore, the insights gained from monitoring IPv6 networks, though limited compared to IPv4, have highlighted the need for more robust security measures as IPv6 adoption continues to grow.
Reflecting on the project's progress, the findings and lessons learned have set a solid foundation for future planning. APJII and its stakeholders can now plan to implement similar honeypot systems at other members' premises, expanding the threat visibilities across different locations and networks. The success of the HoneyV6 ID project also emphasizes the value of collaboration between academia, industry, and community organizations, showcasing how such partnerships can lead to both practical security improvements and enhanced technical knowledge.
Bibliography
https://makassar.tribunnews.com/2024/02/09/apjii-pasang-peogram-honeypot-bantu-cegah-hacker-di-pemilu-2024 (This article discusses APJII's initiative in deploying honeypots as part of its cybersecurity infrastructure to detect and mitigate cyberattacks during the 2024 elections in Indonesia.)
https://www.instagram.com/apjii/p/C9tjuYZTC3b/ (A post highlighting the collaboration between APJII and SGU to utilize honeypot technology for detecting and preventing online gambling activities in Indonesia.)
https://rakyatsulsel.fajar.co.id/2024/02/09/apjii-sulampua-siap-ambil-peran-sukseskan-pemilu-2024-tanpa-hacker/ (An article explaining how APJII leverages honeypot technology as part of proactive measures to maintain network integrity during the 2024 elections.)
This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 


