TECHNICAL REPORT
| Grantee |
SWISS GERMAN UNIVERSITY (SGU)
|
| Project Title | Honeynet Threat Sharing Platform |
| Amount Awarded | US$20,000 |
| Dates covered by this report: | 2020-01-15 to 2020-06-28 |
| Report submission date | 2020-06-28 |
| Economies where project was implemented | Indonesia |
| Project leader name |
Charles Lim
|
| Project Team |
Kalpin Erlangga Silaen
[email protected]
Andi Yusuf, M.T.
[email protected]
|
| Partner organization | Indonesia Honeynet Project, Badan Siber dan Sandi Negara |
Project Summary
With the continuous rise of cyber security threats, monitoring security potential threats and attacks become essential to plan for cyber defense. Honeypot, a decoy system designed to lure attackers, has been used to track and learn attacker’s behavior. Collecting attacker’s interactions with honeypot at different location inside different organization’s premises provide useful and more complete picture of the landscape of current cyber security threats. The log of the attacks to the honeypots become an essential cyber security threat information that could be shared to many of the security incident analyst at different organization to provide a relevant and contextual threat intelligence. The goal of this project is to develop and implement honeynet threat sharing platform that could collect, store, add contextual information pertaining to the threat and share these threat information to the relevant organization. The result of the project will be first implemented in Indonesia then ASEAN and Asia Pacific countries, providing organizations security threat information on a collaborative effort among particating organizations.
Table of contents
- Project factsheet information
- Background and justification
- Project Implementation
- Project Evaluation
- Gender Equality and Inclusion
- Project Communication Strategy
- Recommendations and Use of Findings
- Bibliography
Background and Justification
Swiss German University (SGU) signed a Memorandum of Understanding (MOU) with Badan Siber & Sandi Negara (BSSN) on the 28th November 2018 to collaborate on research in two major areas: Malware and Threat Intelligence. With the honeypots installed on different organizations in various provinces of Indonesia. We need a platform that can provide repository for the security threats captured by these honeypots and share threat intelligence to all relevant organizations at different provinces. Previously, most of these security threats collected from honeypots were not shared in any way and they are used locally by the relvant organization that implemented these honeypots. The project currently have categorized security threats from SSH, SMB, Web, Database services, etc. in the form of Indicator of Compromises, which include IP addresses, URLs, and hashes of binary captured by installed honeypots. With the avilability of this platform, security threat information could be shared to different provinces in the country, the overall security posture of a province or a region can be potentially raised. With the collaboration effort between interested organizations and comunities, the project provide means to raise the involved researchers to be more aware of cyber security threats and how to share them more effectively. This means more people will be involved in collecting, analyzing and sharing the security threats captured by the honeypots, the delta of change of this effort will be multiplied greatly.
In addition, to be useful the security threat information need to be correlated not only among the data captured from different honeypots as well as other open source threat intelligence from around the world. We will propose the enhanced platform that include this capability in the second phase of the research grant to include ASEAN and/or APAC countries in the near future.
Project Implementation
The objective of this research is to provide a sharing platform for any organizations in Indonesia (later can be applied to ASEAN and/or Asia Pacific countries) to share security threats information collected using honeypots in the relevant organization in the related countries to other organizations in Asia Pacific. To start with, the research will begin to develop and share the security threat information collected from different provinces to all related organizations in Indonesia. The project is open to any researchers (men or women) who is interested to help building better security posture in their respected countries or any Asia Pacific countries. The completed project is expected to bring significant contribution to raise not only the participation of security threat information contribution but also the overall potential security posture of the Internet in Asia Pacific.
This is the first time we combine research effort between government, education institution and cyber security community to build a security threat information platform. As expected, the team member from each organization or community is expected to contribute ideas, efforts and time to ensure the project is completed as proposed. We have to change our original design from distributed model to a more centralized after several experiment trying to handle huge traffic from all participating honeypots. The orirginal design also put MISP as the central processing and correlation for all our captured honeypot data, as shown in Figure 1.
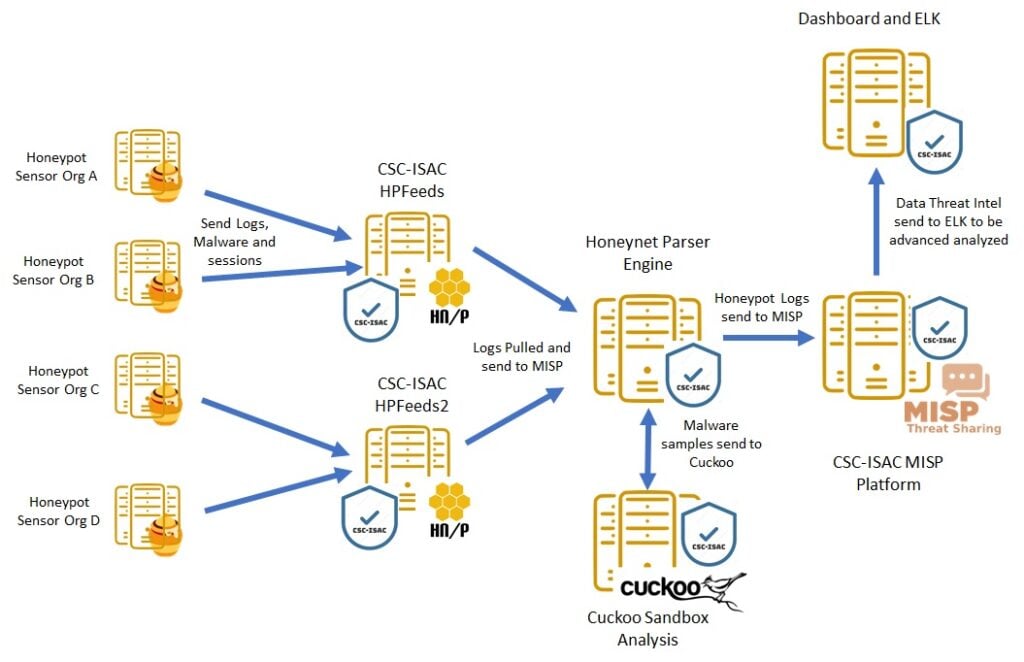
Figure 1 Original System Design Architecture (Distributed)
During our preliminary testing phase, we found out that MISP database is not suitable (due to the slow performance) for our purpose, since our final goal is to able to support huge data collected from large scale deployment of honeypots. Figure 2 shows the new system architecture, in which the processing of the collected threat information is now centralized and we use the concept of data lake to host all the categorized honeypot data.
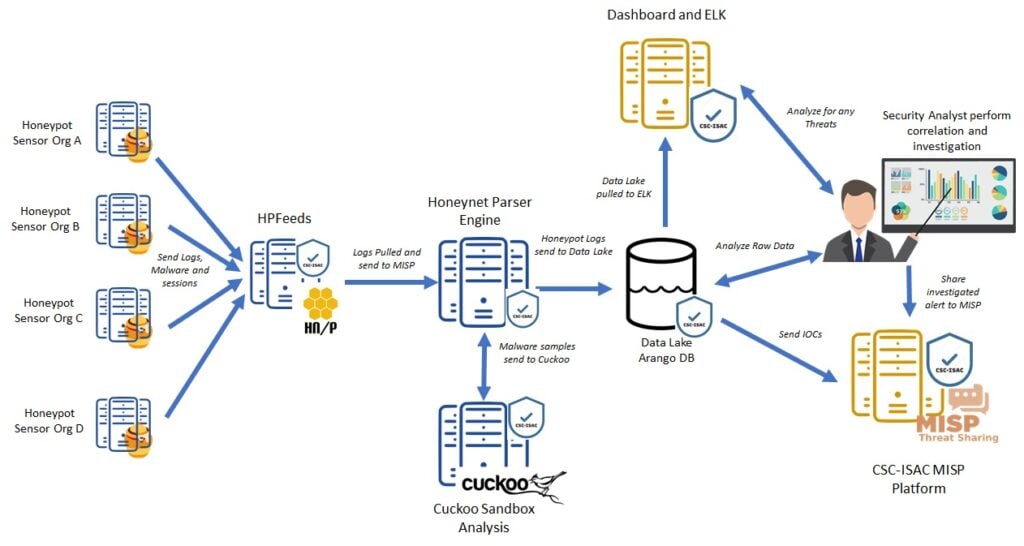
Figure 2 New System Architecture (Centralized)
On the project administration, since January 2020, we moved our regular meetings to online meetings due to challenges to find the right time to meet for every members (students, alumni, government officials, professionals). This decision also eases our collaboration works during the pandemic started in March 2020, allowing all of us working from home. We maintained all our documentation and meeting results using cloud storage, in which everyone is able to contribute on the documents. The user documentation for the project is now online and the team members keep revising the documentation as the time goes (https://csc-isac.readthedocs.io/en/latest/). Docker file for this project is also now online for public use (https://github.com/csc-isac)
During the development of both public dasboard and internal dashboard, we found out that our server's RAM and Hard Disk type we have procured can not keep up with the requirement of huge requirement of I/O access due to the large amount of honeypot data collected from participating sites. The additional SSD disk we added helps increase the query performance for our huge data (about 1.2 million attacks for every 24 hours based on 8 pilot honeypots). The additional RAM for the server is still on its way, at the time of this writing, in which the performance will be further improved once the RAM is installed. Public dashboard for our project can be accessed at https://dashboard.cscisac.org/ (currently still require authentication to access) and below are the screen capture of the portal.
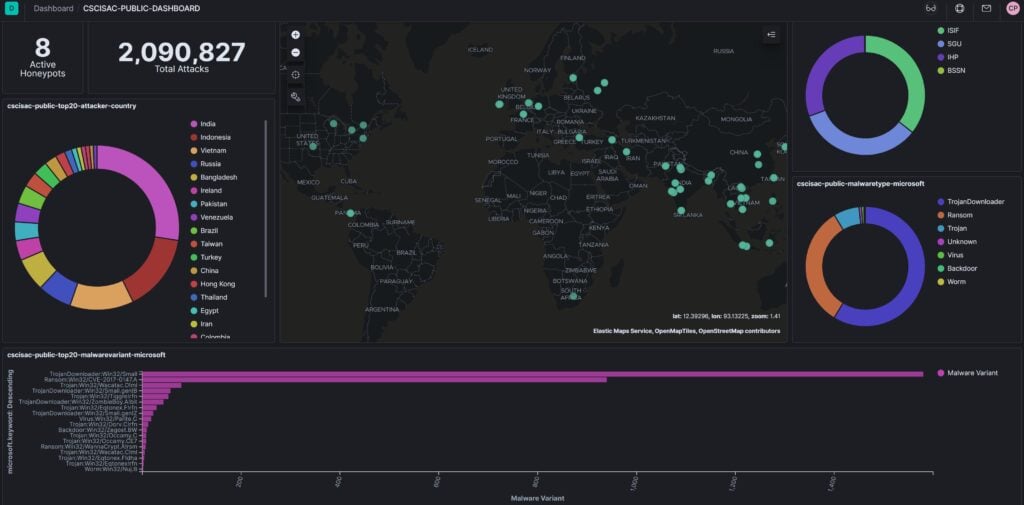
As planned, we always involved a few undergraduate students (men and women) in our project, and as expected some students performed well, while other is under performed in completing the allocated tasks. We ended reallocating tasks to a better performed students in order to complete the scheduled tasks on time. Nevertheless, we are glad to have 2 women (one undergraduate student and one professional) to participate in our project, they performed quite well in their given tasks.
Our project management experience also demonstrated to our Academic Research Community Service (ARCS) department that it is possible to manage the team well and independently (including the financial matters related to the project) while collaborating with multiple institutions at the same time. All parties are all very happy with the progress of our project even tough we are challenged by some limitation of accessing the lab for almost 3 months due to the pandemic. We are also grateful that we have designed the lab to be accessible through VPN from day one of operation, in which helps our team in working with system installed around the clock as required.
Project Evaluation
Following are the project lesson learned during the design and development of honeynet threat sharing platform:
- The project demonstrated that the triple helix, introduced by Prof Henry at Stanford U. - http://ojs.stanford.edu/ojs/index.php/intersect/article/view/849), works. In our case, the institutions involved are higher education, government and cyber security community.
- We are glad that we have at least 2 women as part of our team members in the project, allowing diversity as part of our project
- With the stable platform (after some few months testing), we are now more comfortable to promote to multi stakeholder to participate in our project this year. Leveraging IHP communities and BSSN multi stakeholder will be aim for this year implementation tasks.
- Equipped with the 2-day threat analysis capability training in December and more experience with threat categorization and analysis, we are now more confident to share to the public our experience, raising the bar on threat analysis capability to the next level.
- We have discovered the most suitable distributed model for threat sharing for current and future needs (allowing participants from different countries of ASEAN or ASIA PACIFIC). This model allows correlation of data in data lake farm providing future of many related research possibilities in the future, as shown in Figure 1, our roadmap.
- Operational challenge to maintain this platform is the key success factor, since we need to maintain a team of analyst to continuosly analyze the traffic for the unknown threats, not categorized by the system automatically.
- Another operational challenge is to continuously fine tune and possibly update the system (hardware upgrade) to provide better performance when working with the system, given the volume of attacks will increase exponentially as more honeypot data are fed into the system for analysis.
- This is the first research project, in which all the project members learned together how to develop the platform to solve the real problem using open source software. In addition, all members also are forced in a good way to work with dockerized system components supporting the platform, minimizing the impact when upgrading certain component in the system.
- Even tough it is a big challenge to manage team virtually in the pandemic, every team members learn to be punctual for the meeting, realizing everyone has his/her own tight meeting schedule to attend. Hence from the project management aspects, ensuring every members completed assigned tasks on time is the key succes factor of the project.
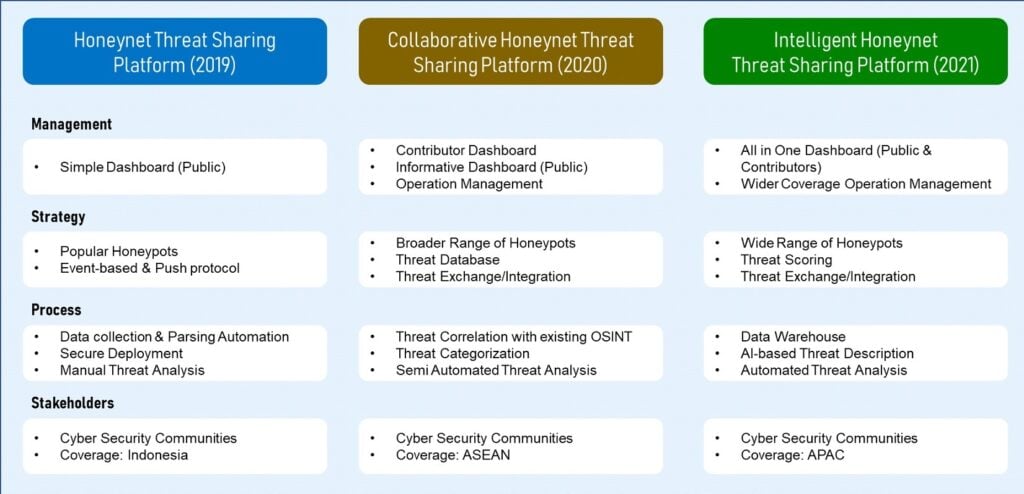
Figure 1 Honeynet-based Threat Sharing Platform
| Indicators | Baseline | Project activities related to indicator | Outputs and outcomes | Status |
|---|---|---|---|---|
| How do you measure project progress, linked to the your objectives and the information reported on the Implementation and Dissemination sections of this report. | Refers to the initial situation when the projects haven’t started yet, and the results and effects are not visible over the beneficiary population. | Refer to how the project has been advancing in achieving the indicator at the moment the report is presented. Please include dates. | We understand change is part of implementing a project. It is very important to document the decision making process behind changes that affect project implementation in relation with the proposal that was originally approved. | Indicate the dates when the activity was started. Is the activity ongoing or has been completed? If it has been completed add the completion dates. |
| Delivery Time | Software Beta Ver. | Docker Development | The Delivery was late by 2 weeks | Completed (15 Mar 20) |
| System Tested | Dashboard Beta Ver. | Load Testing | System Crashes several time, due to slow disk performance. Added SSD | Crash Solved (SSD 5 Jun 20) |
| System Perf Improved | Dashboard Query Speed | Load High Volume Data | Slow Performance due to running out memory space | In Progress (RAM orderd) |
| Number of Participant | Stakeholder Awareness | Promotion | Public Awarenss via Seminar | Completed (18 Jan 20) |
| Number of Participants | Stakeholder Participation | Promotion | Targeted stakeholder to be invited on 22 July 2020 | In Progress |
| Number of Participants | Public Awareness | Presentation | Presentation Project Update in Apricot 2020 | Cancel Participation (due to Pandemic) |
| Publication of Research | Paper Publication | Research Publication | International Journal Paper is still written up | In Progress (Target End of July Submission) |
Gender Equality and Inclusion
Since the beginning of the project, it is a challenge to recruit women who are interested in Cyber Security research to participate in our project. On the average, we have a maximum of 10 percent for number of students who are intereted in cyber security from one batch of students admitted to our Bachelor of IT program. We will be very fortunate to find one woman interested in cyber security for every batch of students. Nevertheless, We are grateful to have 2 women in our research team: one from undergraduate student in SGU dan one from BSSN staff. Technical capability of undergraduate student is also another challenge: need sometime to mentor and train to develop the required skills to perform the work. On the other hand, BSSN staff didn't have any trouble to participate in the research work.
Project Communication Strategy
To raise awareness for our stakeholder, SGU in partnership with IHP and BSSN, conducted a cyber security seminar and workshop in SGU on 18 January 2020. The event is intended to announce our research collaboration, research grant obtained from ISIF Asia and opportunity to participate in our activities. About 160 participants registered both for seminar and workshop, which exceed our expectation (150 planned).
Below is the flyer we use to promote the event.

The other event we would like to participate to expose our project is Apricot 2020, but my departure to the event was cancelled due to the pandemic. To replace public exposure event, SGU is planning to organize an online seminar event on 22 June 2020 to share the latest research results to the public and in particular the stakeholder who will participate in our project. We will also expose the research is possible due to research grant from ISIF ASIA and hope this convince and draw the stakeholder to sign up to participate in our project. The event is open to public, both men and women, to attend with registration and electronic media reporter will be in the event to report the event.
In addition, we also intend to continue to perform more research on different aspect of threat visualization, an important aspect of threat intelligence and publish the research in an academic international journal or International Conference. Hence, this effort increases the public awareness on many fronts, including public in general, government, industries, and acadmics.
Recommendations and Use of Findings
This is a first time our institution received grant from ISIF Asia and we all learned many aspects of managing research project from technical and financial aspects better and better for each round of reporting. Many researchers in SGU are also inspired and motivated with the grant received from ISIF Asia, proving that we all have the same opportunity to receive grant from international foundation. Making the research project a success requires many aspects managing people, process and technology as always, this is especially true when we need to provide service to the public and relevant stakeholder we are recuriting. The stakeholder always seek to participate in the project they trust and benefit from the value the project has to offer. Thus, the key success factor is to focus on delivering value to the relevant stakeholder while continue to perform research to contribute in a significant way.
The support from ISIF secretariat has been well managed and responded. When submitting the report, however, it is best to provide mechanism to allow user to preview the report from time to time since creating a report usually takes hours to complete. Another suggestion for the system would be to be able to save document automatically in a periodic manner helps reducing the lost text or diagram being typed in the portal.
Bibliography
These are some of the digital footprint of the event on 18 Jan 2020:
https://www.kalderanews.com/2020/01/ancaman-serangan-siber-semakin-kompleks-dan-canggih/
http://www.smartcityindo.com/2020/01/antisipasi-serangan-siber-sgu-siapkan.html
https://serpongupdate.com/antisipasi-serangan-siber-sgu-siapkan-lulusan-ahli-keamanan-siber/
https://infobisnis.id/2020/01/21/menghadapi-ancaman-serangan-siber-yang-semakin-kompleks-canggih/
http://www.pusatrobot.id/2020/01/antisipasi-serangan-siber-sgu-siapkan.html
This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 


