TECHNICAL REPORT
| Project Title | Bug Zero |
| Amount Awarded | 85000 |
| Dates covered by this report: | 2021-12-15 to 2023-06-30 |
| Economies where project was implemented | Sri Lanka |
| Partner organization | Sri Lanka Computer Emergency Readiness Team | Coordination Centre (SL CERT | CC), ISACA Student Group of University of Colombo School of Computing |
Project Summary
"Bug bounty platforms have helped many organizations in advanced economies worldwide, but south Asian countries are yet to exploit that notion fully, and many organizations in this region are suffering from a stereotypical understanding of computer security. Equipped with empirical research data on published results, we have started a bug bounty platform in Sri Lanka - Bug Zero (https://bugzero.io). Project Objectives: To help organizations to make their organizations more secure by introducing the concept of bug bounty platform Bug bounty platforms provide the most cost-effective security testing strategy with a pay-as-you-go cost model. This is a critical perspective for many organizations in the region with largely restricted budgets and staffing, as it provides around-the-clock continuous testing. Recent work on understanding vulnerability management in organizations has highlighted issues in remediation. Bug bounty offered a unique feature in helping organizations fix and validate patches, which, in turn, helped organizations. To build an ecosystem in the South Asian region with better security knowledge. Especially in the South Asian region, it lacks proper security professionals with accredited backgrounds. Even though the region boasts a solid tech literacy and products, surprisingly, we lack proper security professionals. A lack of skillful professionals means organizations cannot afford highly sought-after individuals with proper security backgrounds. Promoting bug bounty created awareness of being a good security tester, which eventually helped build a workforce with better security knowledge. To promote local economic alternatives for many youths and promote inclusion, whereas security has primarily been male-dominated. We helped people become bug hunters by providing materials, guidance, and essential opportunities to work with actual organizations. We acted as a conduit for personnel with interest and especially provided an opportunity to work with a real-world use case through our bug bounty platforms. We wanted to both help them learn and provide the essential platform to connect with real-world organizations. This building the workforce perspective entailed building a skilled workforce and a workforce more inclusive, regardless of gender, economic status, and other factors that hindered many from achieving their goals. We focused more on getting females to excel in security testing and started a set of workshops in rural Sri Lanka to create awareness and help them build a potential future for themselves During this year's project duration, we were able to organize the following activities and achieved the below-mentioned accolades. The full details regarding these activities can be found in upcoming sections. Bug Zero has found 630+ security vulnerabilities in local organizations in Sri Lanka and has helped to fix critical 128 security issues through bug bounties. Have recruited 1300+ bug hunters from 40+ countries to register on Bug Zero as freelance bug hunters. Conducted 11 large-scale seminars for different segments including both local and international audiences to make them aware of the bug bounty concept. Worked with ICTA (Information Communication Technology Agency - the national agency in charge of prompting ICT in Sri Lanka) to promote bug bounty as a viable and economically sound alternative to achieve better security posture for startups in the region through active participation in Global Entrepreneurship Week 2022. Came to an MoU with ICTA to promote bug bounty nationwide. Expanded the project's reach, by registering 12 commercial organizations. Introduced Bug Zero Medium as a knowledge-sharing point to share ICT & cyber security-related information and a mechanism to promote reading, writing, and researching on security among Sri Lankan youth. Getting local recognition as a bronze award winner in the category of security solution provider under the business service category in Sri Lanka at NBQSA National ICT Awards, 2022. Getting nominated for The Asia Pacific ICT Alliance Awards (APICTA) 2022 under the category of Security Solutions for business services."
Table of Contents
- Background and Justification
- Project Implementation Narrative
- Project Review and Assessment
- Gender Equity and Inclusion
- Project Management
- Project Sustainability
- Project Communication
- Project Recommendations and Use of Findings
Background and Justification
Score Lab is a well-known and award-winning research group in Sri Lanka. We have active research collaborations between the International Cybersecurity Institute (ICSI), a UC Berkeley Research Institute, and the Qatar Computing Research Institute (QCRI).
We mainly focus on conducting computer security research. Currently, we are conducting education programs targeting low-income countries through an online Master's program focusing solely on cyber security. Through our affiliation with other universities in developed nations, we saw an opportunity to properly promote security in ways that not only help organizations but also build a skilled workforce that can contribute to the local economies. We felt a bug bounty platform will be an ideal solution to achieve that goal.
What is the problem(s) that the project seeks to solve?
There are several huge misconceptions about using bug bounty platforms. In past research conducted by the Bug Zero researchers, we identified that one of the biggest misconceptions is “How can we trust the bug hunters? And, do we attract unwanted attention with a bug bounty program?”
In reality, any system with any sort of public-facing component is constantly scanned and scrutinized for security vulnerabilities with the malicious intention of harming the organization. Over and over again, prior incidents have reminded us that there are no perfectly secured systems globally, therefore, the chances of a malicious user getting into the system is quite remarkable. Therefore, with or without utilizing bug bounty programs, the public-facing systems of any organization are in constant danger.
With the usage of bug bounty platforms, organizations can add another element to the equation to balance out the situation. Along with the malicious users, there are also security researchers competing with each other to find vulnerabilities not to harm but to get a reward, or they genuinely want to help the organization. The basic motivation for these bounty hunters is the glory of discovering a vulnerability in a reputable system and getting remembered for it. Regardless of the time, it takes to fix a vulnerability, this allows organizations to learn about their security issues and prepare them or give them time to remediate these vulnerabilities as soon as possible.
Another common misconception is, “we run a sensitive business; how can we allow strangers to test our systems?”. As mentioned earlier, the strangers are already trying to find loopholes in those public-facing systems. However, bug bounty platforms will not add an extra threat surface to the system. Rather, they allow ethical hackers to try to find vulnerabilities. In addition, bug bounty platforms offer private bug bounties that allow organizations to vet the bug bounty hunters and invite them to in-house hackathon style vulnerability testing. This allows organizations to keep a tab on who is testing which components.
The Pentagon, the headquarters of the United States Military which holds huge amounts of the most secure data in the world, has embraced bug bounty programs since 2016. They have discovered thousands of security vulnerabilities in their systems through private bug bounty programs.
Some of the biggest technology companies such as Google, Facebook, and Microsoft, have embraced bug bounty programs and they have rewards over millions of dollars as bug bounties. The Bug Zero platform is capable of catering to Sri Lankan organizations that are in need of a bug bounty platform to host their bug bounty programs.
At the Bug Zero platform, we strive to provide innovative solutions to organizations and help them in securing their software assets. In addition, the continuous collaboration between the organizations and the Bug Zero platform makes the bug bounty ecosystem safer and friendlier and reduces the barriers to entry into bug bounty platforms. The notion of a homegrown bug bounty platform provides more confidence to Sri Lankan organizations to work with us and achieve their organizational security goals.
What is the motivation of your organization and team members to do this project and offer a solution?
A bug bounty is probably the latest addition in the realm of alternative security testing. In the South Asian region, there are already many security organizations selling various products and services such as pen testing, monitoring, red teaming, etc. However, most of the time, organizations do it without a proper internal setup and understanding of each different testing strategy. Most of these organizations in the region have restricted budgets and staffing resources. Hence, high-end, expensive security solutions are unlikely to last in the ecosystem.
Moreover, while these services and products bring something valuable to the table, we want to understand how to create more jobs for the region, create a more skilled workforce, and help organizations find more skillful people, which is a scarcity currently in the ecosystem.
To answer that problem unique to the region, we believe bug bounty platforms bring out the best of both worlds. It creates a workforce that can work from home; test real-world systems in their leisure time. This is an attractive incentive for many tech enthusiasts who can learn these traits by themselves (or provided by Bug Zero) and start earning a lot of money. Bug bounty platforms offer a pay-as-you-go model where organizations do not have to invest in expensive security contracts but only pay for what bug hunters find and only if the bugs are impactful. Hence, we firmly believe that bug hunting can help immensely back the economies by being less dependent on foreign products and services and creating a skillful workforce, and eventually and more importantly, it is help organizations be more secure with less money invested in security. We also believe that given the financial and technical interest, this is provide a rare factor to discourage the brain drain of this region.
Project Implementation Narrative
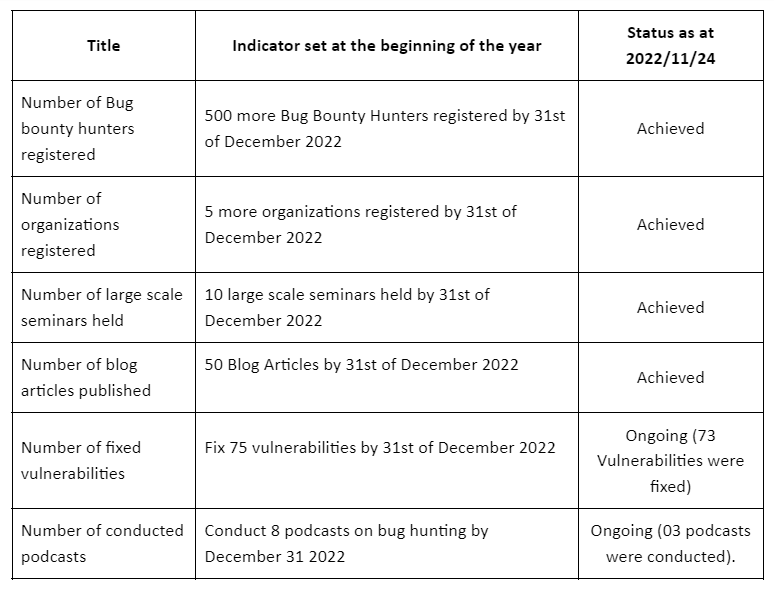
At the beginning of the year 2022, we set a few indicators and baseline actions to execute this project with the aim of building a community of secure testers and convincing the organizations to join the bug bounty platform. The Project Progress Indicator table shows what indicators we had at the beginning of the year and where we are today.
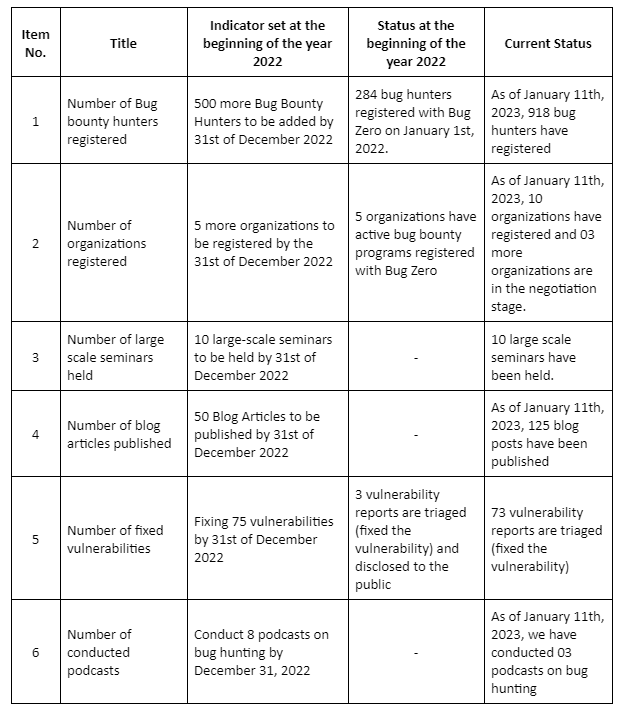
To achieve each of these indicators we have taken several actions and implementation approaches which are mentioned in the below paragraphs. Many of these indicators were achieved with the partnership of the ICT Agency of Sri Lanka (ICTA) and it helps us to reach more users and business communities.
The number of Bug bounty hunters registered
During this year, Bug Zero was able to increase its registered secure tester count by showing around a 524% increase from 248 bug hunters to 1301 bug hunters. The continuous awareness programs on bug hunting and security testing organized by Bug Zero with the partnership of ICTA can be identified as one major reason for the huge user count increase. Throughout the year we conducted 11 larger-scale seminars (full details were provided below) conducted by targeting university students, security enthusiasts, and inclusive communities both locally and internationally.
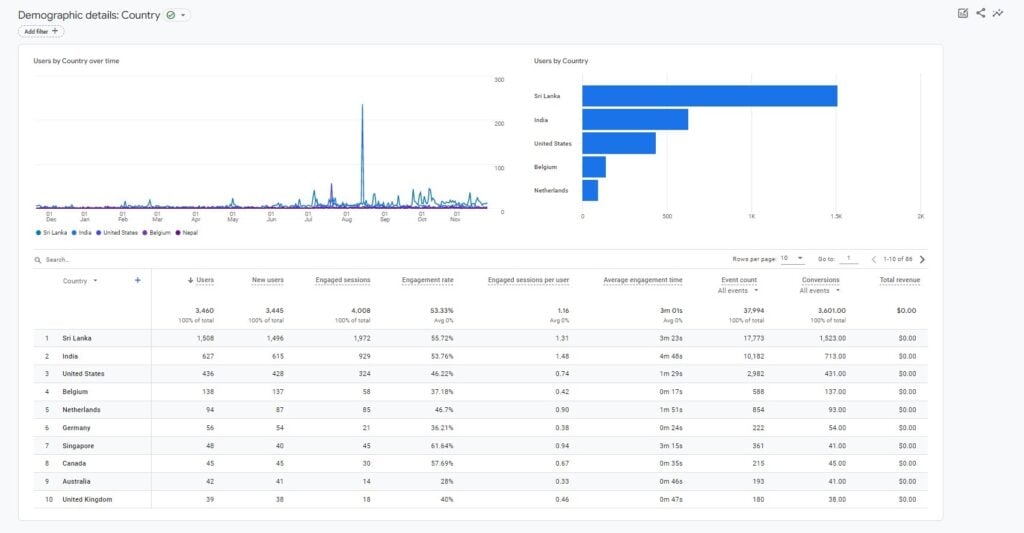
In addition to that, we do have a YouTube channel and we are using that to promote the Bug Zero platform among the community. As a result of this continuous awareness session and marketing campaigns, currently, bug hunters from 60 economies have been registered as hackers and trying to find the vulnerabilities of the available programs. The demographic details of the registered bug hunters are as follows.
- Sri Lanka: 825
- India: 254
- Nepal: 25
- Egypt: 23
- United States: 16
- Bangladesh: 11
- Indonesia: 10
- Pakistan: 10
- Vietnam: 9
- Australia: 6
- Brazil: 6
- Kenya: 5
- France: 5
- Burma: 4
- Turkey: 4
- Morocco: 4
- Iran: 4
- Japan: 4
- Philippines: 4
- Afghanistan: 4
- Italy: 3
- Greece: 3
- Algeria: 3
- South Africa: 3
- Singapore: 3
- Saudi Arabia: 3
- Sweden: 3
- Spain: 3
- United Kingdom: 2
- Colombia: 2
- Sudan: 2
- China: 2
- Thailand: 2
- Malaysia: 2
- Nigeria: 2
- Ethiopia: 2
- Tunisia: 2
- Mexico: 2
- Iraq: 2
- Ukraine: 2
- Argentina: 1
- Belgium: 1
- Albania: 1
- Hong Kong: 1
- Germany: 1
- Solomon Islands: 1
- Poland: 1
- Uganda: 1
- Lithuania: 1
- Russia: 1
- Tokelau: 1
- South Korea: 1
- Cyprus: 1
- Canada: 1
- Portugal: 1
- Cameroon: 1
- Netherlands: 1
- Norway: 1
- Taiwan: 1
- Slovenia: 1
The number of organizations registered
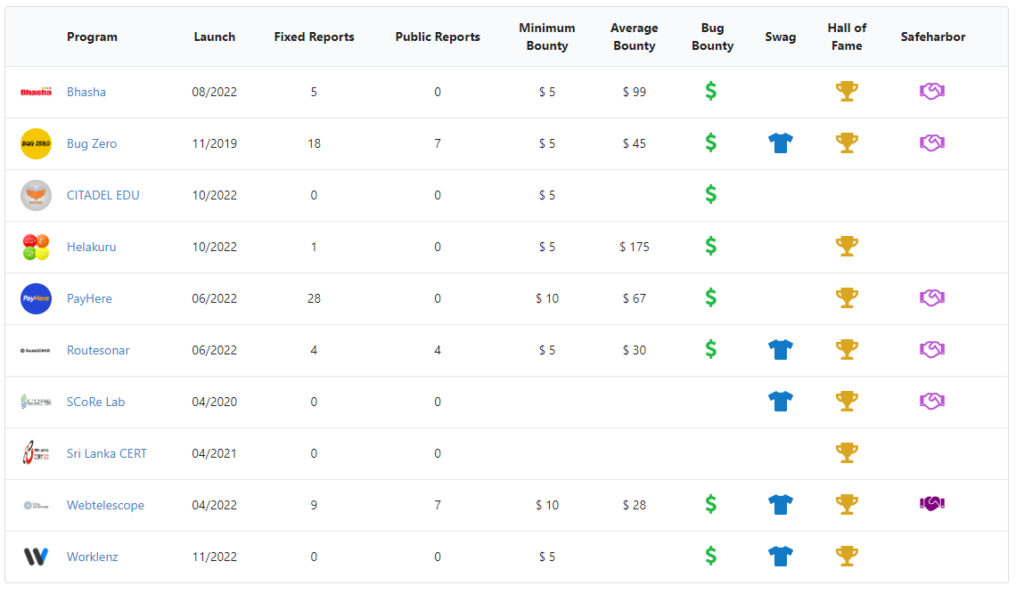
Currently, the Bug Zero platform has 12 organizations registered and two more organizations are in the initial discussion stage. We hope that those two companies will also join us before the end of 2023.
Bhasha - Bhasha is a Sri Lankan Digital Technology Company that offers localized software products for Sri Lanka. Bhasha is the parent company that offers the Helakuru application. It provides services such as HelaPay (a payment application for mobile users), PayHere (a payment gateway) and ShopHere (a service that allows users to set up their own online stores).
Helakuru - Helakuru is a Super app that offers Lifestyle Digital Services to empower Sri Lankan Masses. The Helakuru app has more than 10 million Android users and is a prominent application that is vital for Sri Lankans.
Bug Zero - Bug Zero is a fully managed crowd-powered bug bounty platform that connects organizations with hackers.
CITADEL EDU - CITADEL EDU is an online education platform.
PayHere - Sri Lanka's Leading Online Payment Gateway Service with the largest customer base.
Routesonar - RouteSONAR is a state-of-the-art route optimization platform aimed at planning multiple deliveries for the most efficient, sustainable, and cost-effective delivery.
SCoRe Lab - SCoRe Lab has conducted research covering various aspects of sensor networks, embedded systems, digital forensics, information security, mobile applications, cloud, blockchain, and software tools. The goal of our research is to generate computing solutions by identifying low-cost methodologies and strategies that lead to sustainability.
Sri Lanka CERT - The Sri Lanka CERT Coordination Centre bug bounty program is handled by the bug zero platform. The Sri Lanka CERT is the official government agency for cybersecurity in Sri Lanka. It is the trusted source for advice about the latest cybersecurity threats and vulnerabilities affecting computer systems and networks.
Webtelescope - the Cyber security research team of SCoRe Lab.
Worklenz - A tool for tracking the productive hours of employees. It helps users with resource management, project planning, and time tracking.
Janashakthi Life Insurance PLC - Janashakthi Life is the fastest-growing life insurance company in Sri Lanka and they joined with us to secure their digital solutions.
Drawify - Drawify is the tool to translate your message into an unforgettable drawing, without having to draw yourself!
In addition to those organizations, we are in the final phase of the discussions with a major telco company in Sri Lanka and a digital rider solution provider.
The number of large-scale seminars held
The outcomes of the project activities are the number of seminars and knowledge sharing seminars conducted and the number of participants. Joining forces with ICTA (Sri Lanka) we were trying to promote bug hunting as an alternative income for both IT and non-IT specialized people. As mentioned, these seminars were useful in reaching out to the community and educating them about engaging with bug bounty platforms. Also, we wanted to push bug hunting as a mechanism to reduce the foreign outflow of money for security testing. So far we have held 11 large-scale conferences.
1. Freelancing Bug Hunting Session - 1 Target Audience - Undergraduates of University of Kelaniya, Sri Lanka Number of Participation - 80 Mode - Online via Zoom Date - 2022/08/24
2. Freelancing Bug Hunting Session - 2 Target Audience - Undergraduates of the University of Ruhuna, Sri Lanka Number of Participation - 45 Mode - Physically at the University of Ruhuna, Sri Lanka Date - 2022/09/24
3. Bug Zero - Research on Cybersecurity Session - 1 Target Audience - Undergraduates of the University of Sri Jayawardenapura, Sri Lanka Number of Participation - 50 Mode - Online via Zoom Date - 2022/10/22. YouTube.
4. Bug Zero - Research on Cybersecurity Session - 2 Target Audience - Undergraduates of the University of Sri Jayawardenapura, Sri Lanka Number of Participation - 50 Mode - Online via Zoom Date - 2022/10/23 YouTube.
5. GEW Session 1: Cyber Security & Bug Bounty Target Audience - High School Students Number of Participation - 121 participants attended the session (Including YouTube live participant viewer count) Mode - Online via YouTube Date - 2022/11/14 YouTube.
6. GEW Session 2: Cyber Security & Bug Bounty Target Audience - Undergraduates Students Number of Participation - 61 participants attended the session (Including YouTube live participant viewer count) Mode - Online via YouTube Date - 2022/11/15 YouTube.
7. GEW Session 3: Cyber Security & Bug Bounty Target Audience - For Regional Startups Number of Participation - 40 participants attended the session (Including YouTube live participant viewer count) Mode - Online via YouTube Date - 2022/11/16 YouTube: Part 1, Part 2, Part 3.
8. GEW Session 4: Cyber Security & Bug Bounty Target Audience - For Enablers Number of Participation - 32 participants attended the session (Including YouTube live participant viewer count) Mode - Online via YouTube Date - 2022/11/17
9. GEW Session 5: Cyber Security & Bug Bounty Target Audience - For International community Number of Participation - 72 participants attended the session (Including YouTube live participant viewer count) Mode - Online via YouTube Date - 2022/11/18 YouTube.
10. Session on How to be a freelance Bug Hunter (Collaboration with ICTA) Target Audience - Undergraduates of the University of Kelaniya Number of Participation - 35 participants (72% Male and 28% Female participation) Mode - Physically at the University of Ruhuna, Sri Lanka Date - 2022/12/02 Images: FB Post
11. Bug Bounty Meetup Target Audience - Cybersecurity Enthusiasts Number of Participation - 50+ Participants Mode - Physically at the Hatch Auditorium, Sri Lanka Date - 2023/02/21. More images on a Facebook post.






Number of blog articles published
Beyond just working on bug bounties, cybersecurity more broadly is a topic with a lack of proper awareness and guidance. We wanted to reach out to a wider audience with a blog focused on security and but bounties while promoting young up-and-coming writers to focus on these topics.
The outcome of the project activities was an increase of readers of the Bug Zero Medium blog which is the main platform for knowledge sharing. Currently, we have published 400+ articles. The content of the articles is mainly related to the IT field and we highly encourage the writers to provide articles specifically on cyber security due to the relevancy of this project.
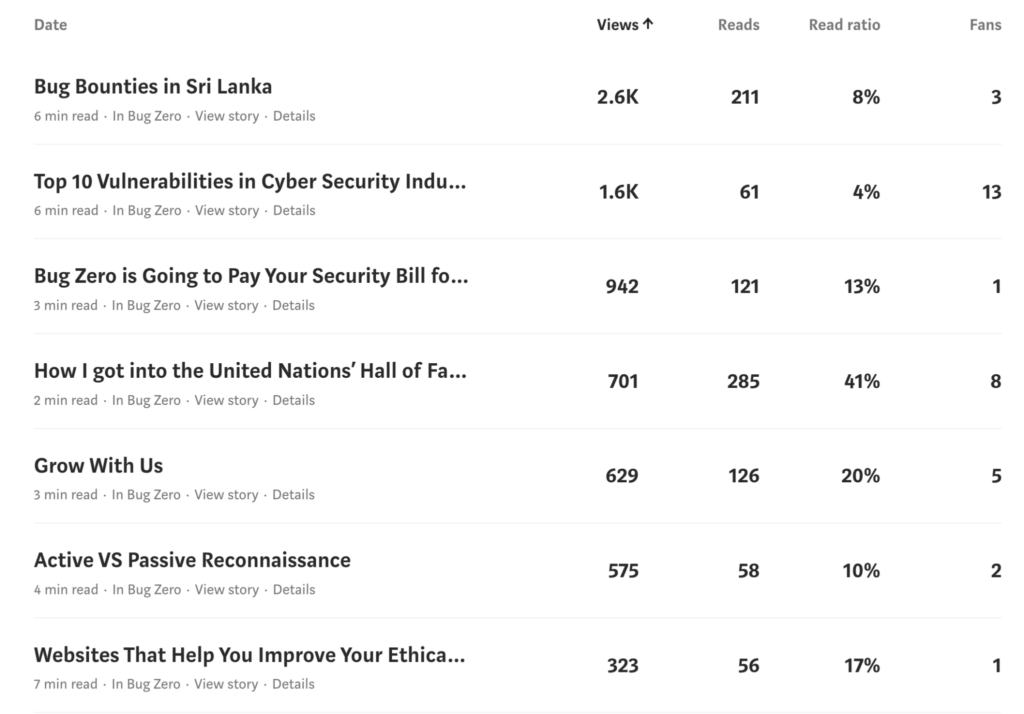
15 writers were actively working with us and we were giving them a financial reward after reviewing the articles based on the quality of the article. Currently, we have awarded around LKR 600,000 for the writers and about LKR 2500 per article as the average. The specialty of these writers is that most of them joined with us during the large-scale seminars we conducted, which shows how much impact we could make in the community, especially among university students. Below are some statistics of what we have reached in the community through this blog in the last 90 days.
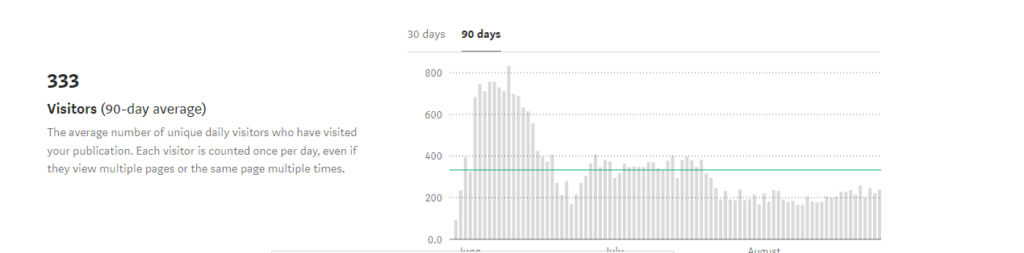
The Bug Zero Medium publication has been read for around 5,004 minutes in the last 90 days. Total unique views across 90 days reached 32,074 users. On average 333 users have visited Bug Zero Medium publication in the last 90 days. A glimpse of the stats from the most famous articles from Bug Zero Medium publication.
The number of fixed vulnerabilities:
The main outcome of this indicator was to increase the knowledge of bug hunters and increase their engagement with bug bounty platforms. Therefore, by evaluating the quality and the quantity of the reported vulnerabilities we could observe the progress of the efforts taken by this project. At the end of June, we got 128 vulnerability reports which are triaged (fixed the vulnerability). Also, for these fixed vulnerability reports we have paid LKR 2,948,500 to the bug hunters during the past five months.
The following are some of the reports that were submitted by the hackers to the organizations which were fixed by them and otherwise they would cost millions of rupees to the organizations.
- LKR 75,000 was awarded for a report which identified the vulnerability of downloading any users’ reports without the proper authentication.
- LKR 75,000 was awarded for a report which identified the vulnerability known as the insecure storage of user data.
- LKR 60,000 was awarded for reporting a vulnerability known as Reflected Cross Site Scripting also known as Reflected XSS.
- LKR 50,000 was awarded for reporting the vulnerability in an admin dashboard where any user can access the admin dashboard without proper authentication.
- LKR 50,000 was awarded for identifying HTML Injection in an Android Application.
- LKR 50,000 was awarded for Server Side Request Forgery in a highly sensitive web application.
Number of podcasts
We conducted three podcasts with the collaboration of the University of Colombo School of Computing ISACA Student Group.
Podcast 1: Topic: iMic Logs - DNS over TLS and DNS over HTTPS Plays: 93
Podcast 2: iMic Logs - What is Blockchain? Plays : 56
Podcast 3: iMic Logs - What is Dark Web? Plays : 36
Bug Zero system development
Since the Bug Zero platform is a constantly evolving platform, we developed new features and deployed them to the users. In addition, our own bug bounty program, receives vulnerability reports and we fix them and publish the vulnerability reports. Our database has all the public vulnerability reports that the organizations have publicly disclosed up to now.
The Bug Zero development team consists of web developers, quality assurance and testers, security analysts, and public liaisons (business analysts). As our development philosophy, we build Bug Zero as a user-centric development cycle. We constantly and continuously acquire feedback from both parties, bug hunters, and organizations. From the feedback we get from hackers and organizations, we deliver new features and obtain user feedback to evaluate them. We improve the components based on the feedback and this is an ongoing process.
Work with Startups
With the exposure we obtained from working with ICTA Sri Lanka, we worked with ICTA Startup Hub, GEN (Global Entrepreneurship Network), Spiralation, and regional startups hubs like UVA Startup Hub which are focused on remote areas with even fewer resources and attention. We were focusing on startups to engage with the Bug Bounty ecosystem based on our research findings. We observed that startups or organizations who are new to the industry are more engaged with the idea of the Bug Bounty Ecosystem and they are keen to understand the ecosystem and get into it. Hence we are promoting our bug bounty concepts to startups such that they would further promote our concepts with their peers also.
In addition, we are planning to approach regional startups such as those located in Maldives to promote the bug bounty concept for their security aspects.
Achievements and Awards
Awarded the bronze award for Security Solutions in Business Services Category at the National ICT Awards, NBQSA 2022. Also, Bug Zero was nominated for the Asia Pacific ICT Alliance Awards (APICTA) 2022 awards under the business services category.

What are the next actions in the pipeline?
Building a knowledge-sharing hub for the Bug Zero Platform - We have already started this action and currently, we are in the process of making educational videos in three languages: Sinhala, English, and Tamil.
We are planning to conduct cybersecurity and technology podcasts targeting school students, undergraduates, and industry professionals.
We are working on the initial steps to start an academy for training Information Influencers (information influencers are a subset of influencers who would find on social media where they spread awareness about cybersecurity, bug bounty ecosystem, and general software development knowledge to their followers). This step is taken since most of the younger generation is keen on social media engagement and their interest in reading written media is plunging in this social media context.
Project Review and Assessment
We believe that the APNIC funding we have received was the major reason for the significant growth of the project during this year. It helped us to organize the above-mentioned activities which contributed to the awareness of the concept of bug bounty in the community which is the primary objective of this project.
As mentioned in the Project Implementation Narrative section, we have been able to achieve almost every indicator we have set for this project so far and we believe that the remaining indicators also we would be able to achieve before the end of the next funding cycle. Therefore, we can say that we were able to achieve the project benchmarks.
When starting this project we basically had three main objectives to achieve through these projects. Below is the description about to what extent we managed to achieve those objectives during this year through the activities we carried out.
Objective 1: To help organizations to make their organizations more secure by introducing the concept of bug bounty platforms.
To achieve this objective, we conducted several cyber awareness programs in partnership with ICTA for non-government and government organizations. As a result of this, we have been able to increase the number of registered organizations from three to seven which is an exceptional growth for a concept like Bug Bounty which is not popular in the region. Now we are looking to expand our growth and reach out to more government organizations while helping them make their organizations more secure. Therefore, we can say that we have achieved this goal at a satisfactory level.
Objective 2: To build an ecosystem in the South Asian region with better security knowledge.
Our continuous awareness sessions targeting cyber security enthusiasts enabled us to promote and market the bug bounty concept to a satisfactory level among the local and internal community. As a result, the bug-hunting community we had at the beginning of the year has grown by 300% in the last few months, which was be a huge positive impact on our objective of building an ecosystem in the South Asian region with better security knowledge.
Objective 3: To promote local economic alternatives for many youths and promote inclusion, whereas security has primarily been male-dominated.
When conducting awareness sessions on bug bounty concepts, we specifically targeted undergraduate students in Sri Lanka who wish to earn income as a freelancer during their studies. So, we gave them a great opportunity to work on our platform as safe hackers to get monetary rewards. In addition, we promote our Bug Zero Medium among the youth to generate additional income by presenting quality content for us. While considering all of these facts, we can say that this objective is also at a satisfactory level.
The included SWOT analysis summarizes the project review under the Strengths, Weaknesses, Opportunities, and Threats we have so far.
The following are the most important findings, outcomes and outputs of the project we found during this year and how we are going to use and promote them in upcoming years.
There is a significant number of Sri Lankan youth who are interested in the concepts of Bug hunting. The only problem we have observed is that the lack of understanding of this concept stops them from focusing on it. However, with proper guidance and educational sessions, we believe we can create a strong ecosystem with a good secure hacker community in the region for bug hunting.
As we observed, in general, most of the companies focus on the internal quality assurance process of their applications which is mainly based on finding non-security bugs and system-level issues. Therefore, some organizations have not fully focused on the security side of their applications and the importance of testing the applications on security aspects, instead of trying to limit flow-level testing and general troubleshooting. We are planning to use this observation as one of our upcoming marketing strategies to promote Bug Zero among organizations. We can inform them of the benefits they can get from having proper security testing and how much it will be cost-effective if they can join with us.
As we have observed in business discussions with organizations, many organizations pay significant amounts to external parties to ensure their application security. The fairness of the returns compared to the amount they spent is highly questionable because many of them face the same security problem over and over again. Therefore, we have a huge potential customer base in the market if we can properly promote the concept of bug hunting among them with the difference of pen testing. Currently, we are studying this gap and how we should address this in our future business discussions.
Even though we have several social media channels to engage with the users, we believe the creative level of the posts and content should be further increased to communicate the bug hunting concepts smoothly to the users. Because of that, now we are focusing more on our marketing side and UI/UX designing side to improve the quality of the content.
As the project team consists of well-experienced researchers in the domain, we are in a good position to discover the latest changes/additions in the industry and map it to configure how to apply them to our platform.
To what extent has the project helped build the capacity of your institution or of the individuals involved?
The Bug Zero Bug Bounty project has played a pivotal role in enhancing both the personality and professional development of the individuals involved, as well as contributing to the capacity building of our institution. Here are some key ways in which the project has had a positive impact:
Certification Support: The project has actively sponsored team members to pursue relevant certifications in the cybersecurity and software development domains. This support has not only boosted their confidence but has also added valuable credentials to their profiles, making them more proficient in their roles.
Regular Meetups and Updates: Bug Zero has consistently organized regular meetups and provided updates on the latest developments in the cybersecurity and internet technology fields. This has allowed our team members to stay ahead of industry trends and technologies, ensuring that our institution remains at the forefront of innovation.
Speaker Opportunities: Team members have been given opportunities to share their expertise as speakers at various events. This not only promotes their professional growth but also showcases Bug Zero's commitment to knowledge sharing and thought leadership in the industry.
Hands-On Experience: Engaging in bug bounty activities has provided our team members with invaluable hands-on experience in identifying and mitigating security vulnerabilities. This practical knowledge has enhanced their problem-solving skills and made them more adept at securing software systems.
Networking Opportunities: The project has facilitated networking opportunities with other professionals in the field. This exposure to a broader professional network has expanded our team members' horizons and enabled them to learn from others in the industry.
In summary, Bug Zero's Bug Bounty project has not only enhanced the technical skills of our team members but has also contributed to their personal and professional growth. Moreover, the project's impact extends to our institution by ensuring that we have a highly skilled and motivated workforce capable of tackling complex security challenges in the ever-evolving landscape of cybersecurity and software development.
Gender Equity and Inclusion
As an organization, Bug Zero actively promotes increasing the percentage of female participation for the event we organized, being aware of the benefits of having a good gender balance within the organization and the cyber security industry. As a part of the project team, we already have a couple of young female researchers involved in our project initiative and we are giving them an equal opportunity to grow themselves within the organization and be a part of our seminar series to make awareness among other females.
Conducted 05 sessions in the GEW’22 event under the topic of “Gender Diversity and Myths in Security” to educate the women's community. These sessions were delivered by one of our young female researchers from the project team.

The WiCSaT 2022 (Women in Computer Science and Technology) was held on the 20th of August at the University of Colombo premises successfully with the participation of undergraduates from the University of Colombo School of Computing and other universities from all around the country. It was organized with the partnership of IEEE WIE Student Branch Affinity Group of the University of Colombo School of Computing to commemorate the 20th anniversary of Women In Engineering.
The celebrations not only empowered women in technical fields but also reflected the key moments, great progress, and achievements made by outstanding women in STEM. The day was filled with informative sessions by experts in the industry, group activities, and also entertaining items.

We have also initiated collaboration with Makers Global for their MakHer initiative. MakHer aims to empower female students and enable them to excel in the STEM field. As part of this partnership, we have designed a program to provide hands-on training to female students in areas such as cybersecurity, web penetration testing, and best cyber practices. Our goal is to inspire and motivate female high school students and undergraduates to explore and actively participate in the field of computer science, with a particular emphasis on the cybersecurity sector.
We at Bug Zero provided equal opportunity regarding gender or race when publishing the medium articles in our blog. The only consideration factor is the quality of the content. Therefore, so far we have published both English & Sinhala articles and we are encouraging our writers to write Tamil articles as well. Also, the fact that five out of 11 writers are women shows the level of equal opportunity we provide.
The most commonly spoken languages in Sri Lanka are Sinhala, Tamil, and English. Therefore, we supported this linguistic and cultural diversity as part of the project team and within the communities. Our project team consists of members who can communicate in these languages. Also, we conducted our sessions in both Sinhala and English. To cover the Tamil community, we are planning to create a knowledge hub that will also feature Tamil educational videos on cyber security and bug bounty concepts.
Bug Zero played a pivotal role in of Global Entrepreneurship Week (GEW) 2022 in Sri Lanka. GEW is a massive movement that is held every November with the participation of around 10 million people all around the world to celebrate and empower entrepreneurs in every country and community around the world. It targets people who face barriers or don't think about launching their own startups to leverage them to come up with new tech ideas to start their own startups. Global Entrepreneurship Week is organized by the Global Entrepreneurship Network and it envisions one entrepreneurial ecosystem open to all, including small towns and underrepresented communities in emerging economies that are systematically marginalized, geographically hard to reach, or otherwise pushed aside or abandoned beyond the high-tech startups. For the event there were around 150 participants and 83% of the participants were male. The majority of the participants were university students and from the age group 20-27.
Project Management
The Bug Zero team is composed of skilled and experienced security researchers and academic professionals who have a lot of experience in managing these types of projects. All the administration tasks and procurement tasks were handled via a central point and we are following work-from-home arrangements for this project. The Bug Zero development team was well versed in secure software development best practices and the internal collaboration between the Bug Zero development team ensures that each other is working up to the industry standard.
Bug Zero has the following staffing roles in 2022 including several casual and contract roles.
- Directors
- Chief Technology Officers
- Software Engineers
- UI/UX Engineers
- Technical content writers
In the Bug Zero recruitment strategy, we explored the prominent bug bounty hunters who are constantly engaging with our platform with valuable vulnerability reports. For those who stand out we offer them an internship position such that they can grow with us and accumulate more experience. Also, we offer internship opportunities at Bug Zero to whom we recognize as potential candidates via our bug bounty platform. In addition, we receive internship applications from candidates who have expressed interest in working with the Bug Zero bug bounty platform and we are currently assessing their candidacy for the internship position.
The Bug Zero team consists with software development interns, cybersecurity interns, technical content writers (Bug Zero Medium Publication team) and community liaisons (such as team members from ICTA Sri Lanka, Sri Lanka CERT|CC and ISACA Student Chapter of UCSC). With these community we contribute to the progress and development of Bug Zero platform and with producing podcasts, blog articles for the BZ Medium Publication and arranging knowledge-sharing seminars and workshops.
The below are the primary project management team behind Bug Zero.
Isuru Vishwanath - Isuru Vishwanath is a vulnerability remediation analyst and also a bug bounty hunter at Bug Zero. He has years of experience in identifying and exploiting vulnerabilities in web applications and mobile applications. Over the years he helped many organizations by finding security vulnerabilities in their systems. He researches vulnerability types and new attack vectors for them.
Januka Dharmapriya - Januka Dharmapriya is an experienced business analyst in the InfoSec domain and a member of the Bug Zero architecture team, providing research insights into the product. He also has a research background in data classification and machine learning.
Nipuna Weerasekara - Nipuna Weerasekara is an experienced web application developer and is also a member of the Bug Zero architecture team. He researches open-source software vulnerability discovery and remediation. He has hands-on experience in cracking web applications.
Ravindu De Silva - Ravindu is a security researcher and innovator. Network and system security are his primary research interests. His research contributions have received widespread international acclaim from tier-one conferences and Journals. Ravindu is a core member of a few global research groups including the globally recognized Bug Zero project. Further, Ravindu is a very good Chess player as well.
Charitha Elvitigala - Charitha Elvitigala has over eight years of experience as a researcher. He also works as an open-source software and security specialist. He is leading the Bug Zero platform team. His collaboration with international research groups helps us to enrich products with new insights from the domain. He has several international publications in security and has expertise in digital currency and money laundering.
Kenneth Thilakarathna - Kenneth Thilakarathna is a consultant, trainer, and practitioner in the domain of information security. Having over ten years of industry experience in reputed software development companies in Sri Lanka, he is a well-experienced person on Secure SDLC implementations. His insights into information security and exposure to local and international clients make him a practical and robust security practitioner in the domain.
Dr. Primal Wijesekera - Primal Wijesekera is a staff research scientist in the Usable Security and Privacy Research group at ICSI and also holds an appointment in the Department of Electrical Engineering and Computer Sciences at the University of California, Berkeley. His research focuses on exposing current privacy vulnerabilities and providing systematic solutions to meet consumers' privacy expectations. He has extensive experience in mobile app analysis for privacy violations and implementing privacy protections for Android. He was part of a panel discussing mobile privacy at the Federal Trade Commission (FTC), in Washington, DC. He has worked extensively with privacy regulations such as COPPA, CCPA, and GDPR. His work featured in the New York Times, Washington Post, and official Apple reports. His work has also brought in multi-million-dollar litigations against Big Tech for their lack of privacy protections.
Dr. Kasun De Zoyza - Dr. Kasun De Zoysa is a well-known security expert both locally and internationally. He is one of the first Ph.D. holders in the domain of information security in Sri Lanka. He has been appointed as a security consultant in several organizations, both government and private sector. At the University of Colombo School of Computing, he takes initiatives, such as the Center for Digital Forensics, and Master of Information Security degree program, to help the community build strength against emerging cyber threats. He has consulted and helped the biggest financial and corporate entities in Sri Lanka in establishing security.
Project Sustainability
Bug bounties are community driven programs. Once the community is growing and helping out other organizations, bug bounties can survive without an issue. As a platform providing bug bounties, we do not incur any cost after the initial phase of community building and convincing the organizations to join the bug bounty platform.
In the year 2022, Bug Zero entered into partnerships with the below-mentioned institutions and entities to promote the bug-hunting concept for community building and to reach Sri Lankan non-government and government organizations for convincing them to join with the Bug Zero Platform. We believe these partnerships hold the key to a sustainable future and the existence of the project.
SCoRe Lab has partnered with the Sri Lanka Computer Emergency Readiness Team | Coordination Centre (SL CERT | CC) which is the official government agency for cyber security and incident response. SL CERT provides security assessments to government organizations and it provides responses to cyber security incidents.
SL CERT was established as Sri Lanka’s National Computer Emergency Readiness Team by the ICT Agency of Sri Lanka (ICTA) in the year of 2006. The Bug Zero platform by SCoRe Lab has partnered with SL CERT to be the official bug bounty platform for SL CERT bug bounty program. As Bug Zero, with the collaboration of SL CERT, we are planning to further provide support for other government agencies to host their bug bounty programs within our bug bounty platform as well as private businesses to host their bug bounty programs.
The ISACA Student Group of the University of Colombo School of Computing has partnered with the Bug Zero platform to host their official bug bounty program. UCSC ISACA Student Group is the first ISACA Student Group under the ISACA Sri Lanka Chapter. The student group’s aim is to encourage education beyond classroom learning by facilitating students to network and learn from each other while connecting with a supportive group of professionals. The UCSC ISACA Student Group hosted their yearly hackathons and captures the flag events in partnership with the Bug Zero platform where the winners were rewarded for their submissions of vulnerability reports.
Additionally, Bug Zero was the biggest partner of Sri Lanka's Global Entrepreneurship Week'22 which further helped us reach out to the cyber security community in Sri Lanka. Helping strengthen our purpose of building bug-hunting communities both inside and outside the country. With ICTA Sri Lanka we co-organize capacity building drives for students, undergraduates and industry professionals to engage with them and make them open to the cybersecurity field and bug bounty concept as a freelancing avenue to earn income and enhance their knowledge. In addition, we engage with startup ecosystems to promote bug bounty as a prominent method for security testing which is cost effective for the startups.
Bug Zero has covered the bounty prize by utilizing the APNIC grant and the client organizations do not have to pay the bounty prize. However, after the end of the grant Bug Zero is not covering the bounty prizes and the client organization has to cover them and Bug Zero is charging 10% of the amount the client organization decides to pay.
Any back-channel communication between the bug hunter and the client organization to avoid the 10% charge disqualifies the client organization from the platform and it is treated as a contract violation by the client organization.
If the client organization wants the bug hunter to help them with the remediation or validation of the fix, it must be conveyed to the bug hunter as soon as possible. Arrangements can be made to delay the full payment, but it is understood that bug hunters be paid for the additional task of helping the remediation or validating the remediation, or both. Bug Zero still charges 10% of the final amount the client organization pays the bug hunter.
The payment amount has to be a minimum of US $10 per vulnerability report, and the maximum could go up to any value depending on the severity and the impact. The reward can also be a combination of financial rewards, Swags such as company t-shirts and coupons, travel tickets, etc. The client organization has to bear the total cost of the reward regardless of its nature.
Additional to that,
- Program Initiation - US $250
- Private Program per Invitation (if this involves external entities such as law enforcement this value could go up to US $50) - US $25
- Annual Public Program Fee (up to 3 programs) - US $1000
- Per vulnerability report - 10% of the total payment to the bug hunter
- Private hackathon event -Hosting cost per event - US $250
- Per invitation - US $25 (if they have not covered earlier through private programs)
- Privacy consultancy on organizational processes, tools, practices - US $25/per hour
- Privacy incident response - US $50/per hour
- Bug Zero will charge US $20 per hour for the time spent with the client to come up with strategies that better suit them.
However, moving forward beyond the APNIC grant, we are exploring ways to still fund bug bounties for under-resourced and funded organizations, especially targeting low income and small to medium businesses with critical data to protect.
Project Communication
The Bug Zero platform thrives entirely on community participation. Since the Bug Zero platform is connecting security researchers and organizations, we have to reach out to both parties where we need to raise awareness of bug bounty platforms in Sri Lanka. In Sri Lanka as one of the first bug bounty platforms, the notion of a homegrown bug bounty platform is novel to the organizations and to the security researchers as well.
The below image shows the Google analytics for our platform bugzero.io.
By utilizing the power of social media, we are trying to increase the engagement from the community and the following are our social media initiatives.
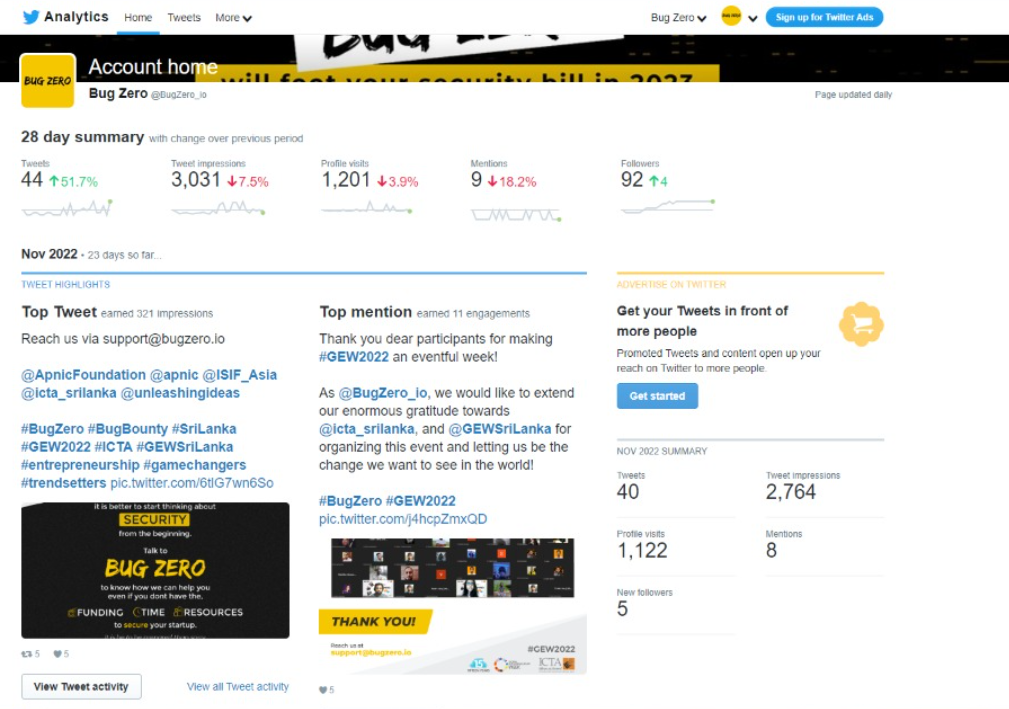
Bug Zero Twitter Account: The Bug Zero Twitter Account provides followers easy access to this software and security-centric Twitter accounts. The basic functionality of the Bug Zero Twitter Account is that it follows Twitter accounts that provide software development and software security-related news and articles, and then the Bug Zero Twitter Account retweets these tweets. We have been using this Twitter Account to update our audience on a vast number of Twitter accounts that provide valuable information.
For example, the following Twitter accounts provide valuable information on their respective areas.
- https://twitter.com/CVEnew - Notify the community of new Common Vulnerabilities and Exposures (CVE) IDs.
- https://twitter.com/CVEannounce - Notify the community of CVE related announcements.
- https://twitter.com/owasp - Provide information about the Open Web Application Security Project (OWASP) and their announcements. (This account is a must follow for any software developer or a security researcher).
- https://twitter.com/ExploitDB - Provides information on security related papers, security exploits and announcements.
- https://twitter.com/offsectraining - Provides information and career guidance in information security.
- https://twitter.com/NullByte - Provides news on new technologies, hardware, and software.
As mentioned in the above Twitter accounts, there are many other accounts to follow by any up and coming security researcher or software developer. The Bug Zero Twitter Account provides access to all these accounts and it reduces the barriers to entry into the security researchers’ ecosystem.
The following are the social media reach and engagement stats, profile visits stats and such for the Bug Zero twitter account.
According to NapoleonCat, there were 7,968,000 Facebook users in Sri Lanka in June 2021. While 36.1% of these users were female, and 63.9% of these users were male. (https://napoleoncat.com/stats/facebook-users-in-sri_lanka/2021/06). This indicates that Facebook can be used as a medium to share knowledge as a Facebook Page. For This task, we are using 02 Facebook pages named Bug Zero Digest & Bug Zero, which provide information regarding software security, new and up and coming technologies, software development best practices and general computer safety tips.
According to Cybint, 95% of breaches recorded are caused by human error. This indicates that if the community is educated on computer security best practices, most of these breaches can be avoided. Even though it is a known fact that using common and guessable passwords are highly insecure, many people still use them to secure their accounts. We believe by community engagement using the Bug Zero Digest Facebook page, we could educate the community on the dangers and pitfalls of bad computer security practices and the value and necessity of following best practices on computer security.
The following are the social media reach and engagement stats, participation stats and such for the Bug Zero facebook page.


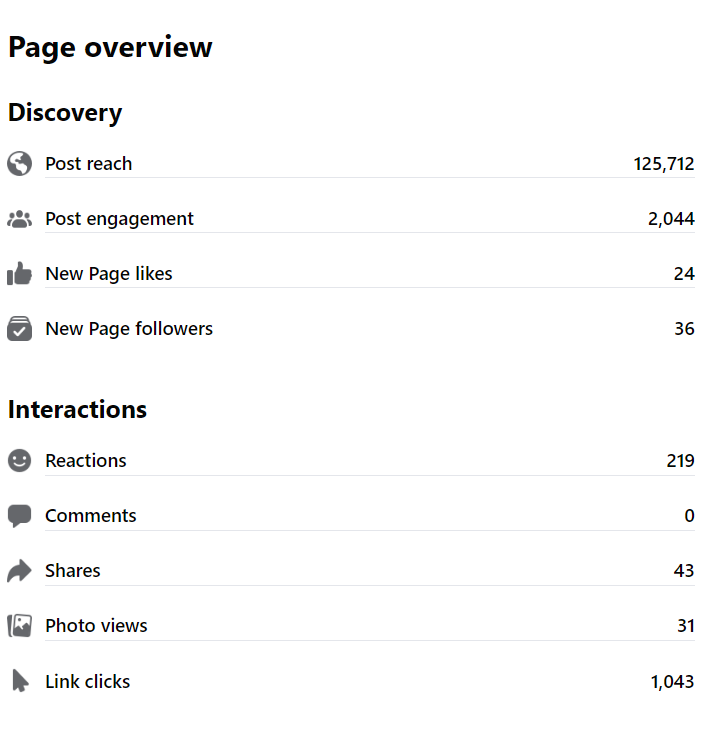
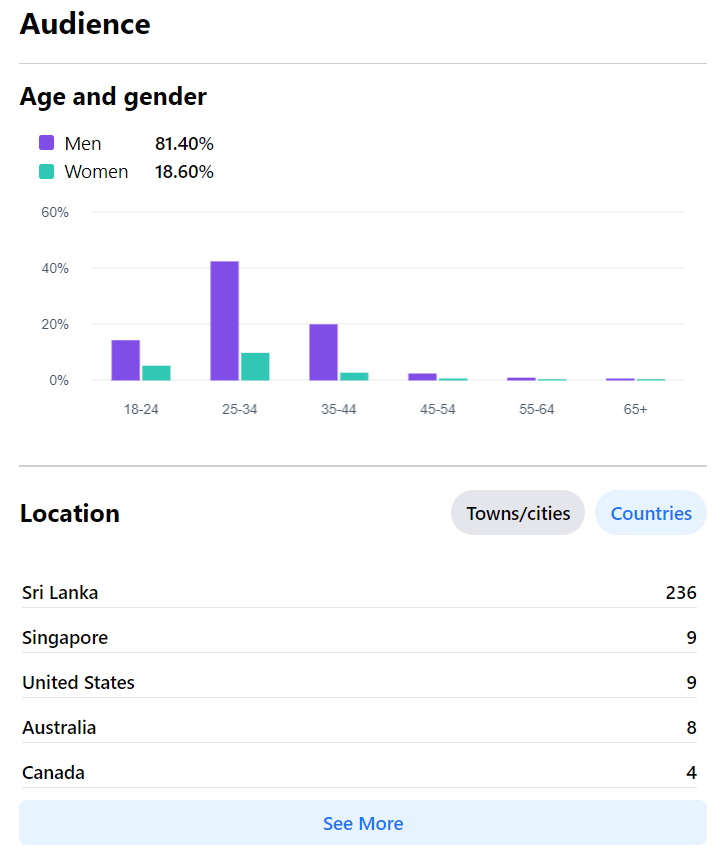
According to NapoleonCat, in June 2021, there were 1,412,000 Linkedin users in Sri Lanka and 58.7% of the user base is from ages 25-34. Since Linkedin is widely accepted as a social media platform for professionals, the young working population of Sri Lanka is the majority of the Linkedin platform user base. In the modern social media context, Linkedin users tend to share educational material on their profile feed in Linkedin. This is a very good indication that people in fact use Linkedin as a platform to share professional information rather than using it for entertainment or other networking purposes. Therefore, we utilize this opportunity and the Bug Zero Digest (Linkedin) came into play by sharing the latest information about software security, software development best practices, career guidance materials on the information security industry, and computer safety guidelines.

Following are the social media reach and engagement stats, participation stats and such for the Bug Zero LinkedIn profile.
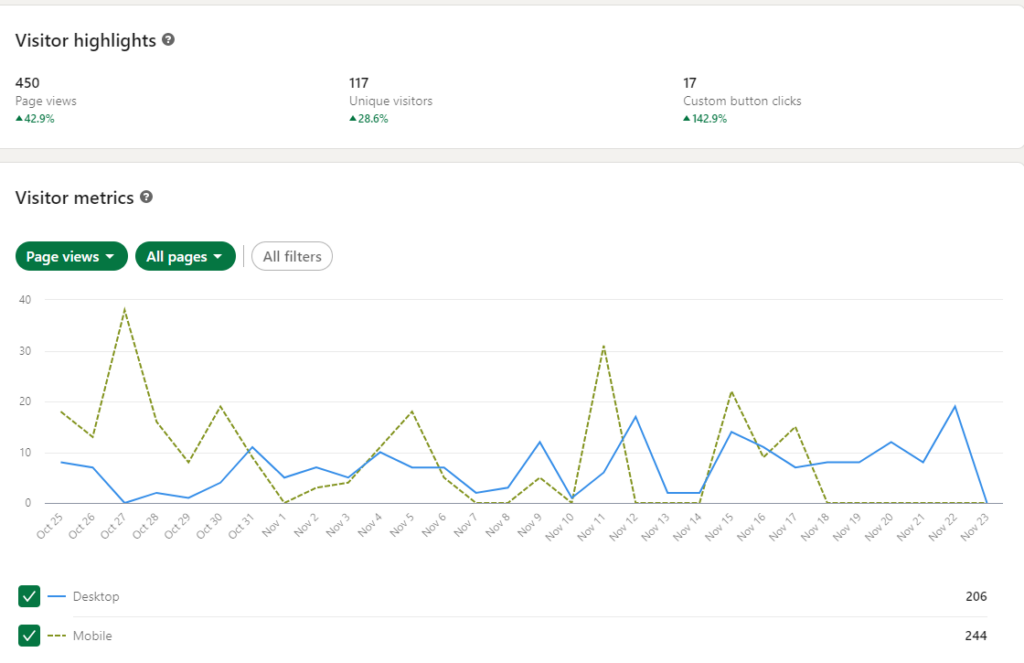
Medium
Medium is a world renowned online publishing platform which connects a vast number of readers with a vast number of independent writers. The Medium blogging platform is a good place to share knowledge regarding software security and information regarding computer security best practices. Currently, there are many online publishing organizations in Medium that share knowledge by providing articles on “How to” and “Do It Yourself”. By utilizing this trend, we share knowledge on a daily and weekly basis. The readers can subscribe to the Bug Zero Medium publishing in Medium and they can read at their convenience.

For the past 90 days, the following are user engagement statistics with Bug Zero Medium. The total number of views for publication has received on all posts and pages - 32,074 The total amount of time spent reading our publications - 5004 Minutes The average number of unique daily visitors who have visited our publication (Each visitor is counted once per day, even if they view multiple pages or the same page multiple times.) - 333 Visitors
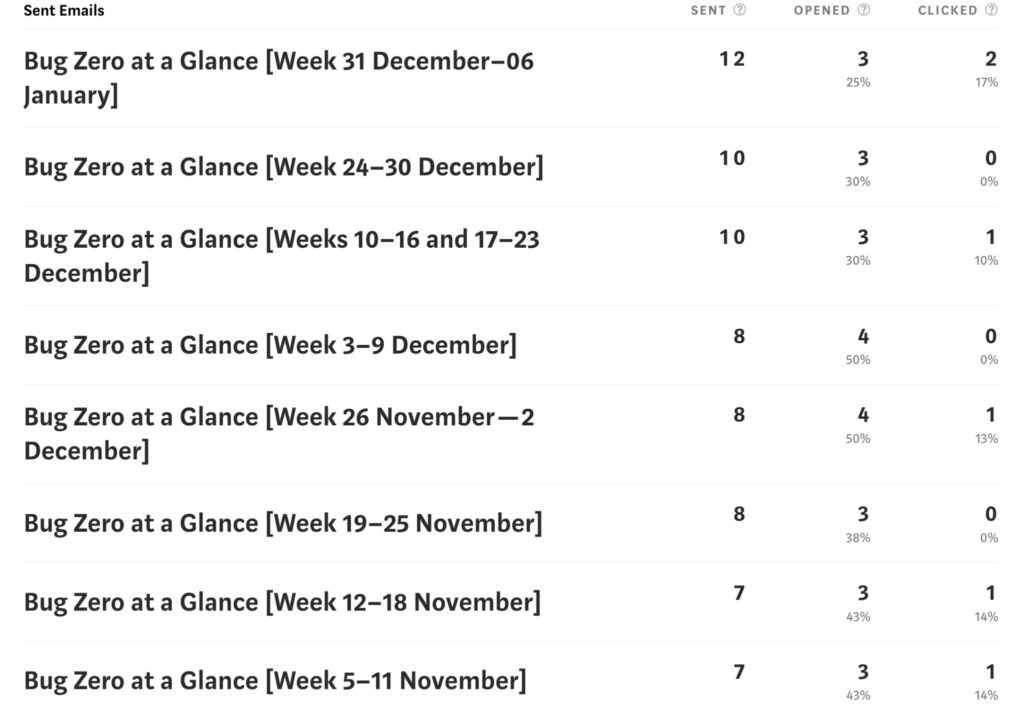
Newsletter
The Bug Zero Newsletter is another initiative that we are using for the users of the Bug Zero platform. The registered users in the Bug Zero platform can opt-in for the weekly and monthly Bug Zero Newsletter where we compile all the security related news and send them out to the subscribers weekly and monthly. We believe continuous user engagement is the key to customer conversion and one of the easily accessible methods is to utilize the newsletters to retain the interaction between users and the Bug Zero platform. According to Marketing Insider Group, the average open rate for an email newsletter in the Education and Training category, is around 22.00% and it is around 20.95% in the Software and Web App category.
This provides a good insight into the prospective effectiveness of the Bug Zero Newsletter. In addition, upon receiving the community feedback about these initiatives, we could enhance our user interaction strategies and increase the open rate for Bug Zero Newsletter. The following are the stats for the Bug Zero newsletters that we published so far.
YouTube
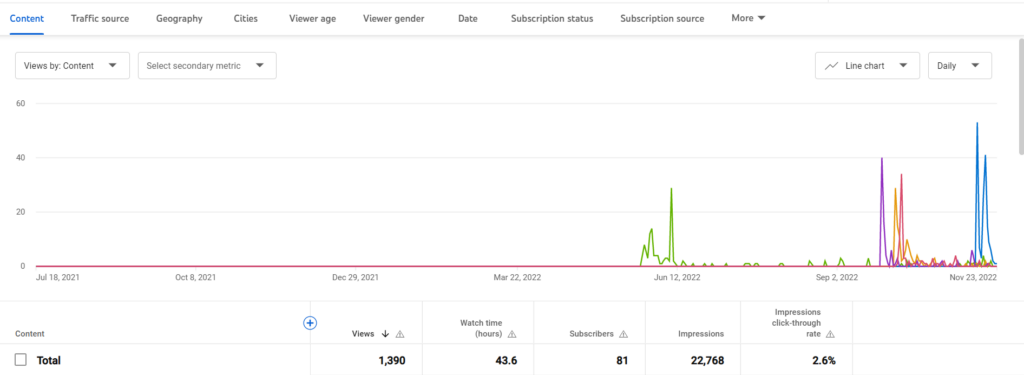
The Bug Zero YouTube Channel features the Bug Zero platform’s user training videos and research presentations. Since YouTube users in Sri Lanka are ever increasing and YouTube is freely available to anyone with internet access, it is a good medium to share knowledge. We plan to share tutorials and discussion videos regarding computer and software security, privacy implications in software, and general software and computer usage best practices.

The following figure shows the channel analytics of the Bug Zero YouTube channel.
Bug Zero Outreach
Internet penetration in Sri Lanka is 50.8% which means, the current socio-economic state of Sri Lanka restricts some people's access the Internet. As Bug Zero, we acknowledge this digital divide as the main issue in Sri Lanka and we act to do our part in reducing the digital divide. All of the modes of communication we mentioned above are based on the Internet. However, there are many people in Sri Lanka who wish to learn new things, educate themselves on new technologies, and become the best versions of themselves.
The issue here is that they do not have access to proper education materials and basic access to the Internet. Since in the current economic and societal context, most of the communication modes are transformed online, people have moved on to online methods such as the Internet, email, and the world wide web for communications. However, if we can reach the people who still have no Internet access, we can reduce the digital divide and let the community thrive. As the Bug Zero Out-Reach proposes, we visit in place to educate students on computer literacy and software development. By utilizing our resources, as Bug Zero Out-Reach we are delivering the knowledge to them rather than making these communities search for knowledge. We have conducted educational seminars and workshops to enhance computer literacy, education on software development and basic computer and IT knowledge.
Bug Zero Research
As Bug Zero is prominently engaging with cybersecurity researchers and engaging with academia, we are studying the bug bounty platforms and their effectiveness. With this regard, many commercial bug bounty platforms are reluctant to let academics on their platforms for academic purposes and due to this the issue is not discussed in depth. However, given our academic background with unprecedented access and experience, our work will cover most of the new topics on client organization initial reactions, how bug hunters communicate and their frustrations and how to mitigate common misconceptions are studied in depth by our research team. We believe our publication will pave a new research avenue and especially help new organizations when they get on board with a bug bounty platform.
Project Recommendations and Use of Findings
We would like to express our sincere gratitude to APNIC Foundation and ISIF Asia Fund for their immense support and generous research funding for this project. It allowed us to scale our project from where we were at the beginning of this year and helped us reach our project goals. We are very grateful to receive this grant from the APNIC Foundation even though we are in financial crisis as a country, it has enabled us to take forward our project of socializing the concept of bug and bug hunting in the South Asian region in a timely manner.
Reflecting on our project progress and activities in the past months, we can safely say that there is a large audience in Sri Lanka and the South Asian region who are passionate about cyber security. If they have proper guidance and support as we have provided them in the last two months, they are very keen to learn the concepts of bug hunting as it is a good source of income and a platform for learning the cyber security concepts for them. However, as we've seen when it comes to bug hunting or crowdsourced security testing, many organizations are under the illusion that their applications will be hacked and open to even more vulnerabilities.
Therefore, we still see a gap that we need to address when it comes to increasing the awareness of organizations to register on our platform by educating them on the concepts of bug hunting. Based on our project experiences and findings throughout the year, we would like to suggest the following recommendations for other practitioners or researchers in the field facing similar problems or to focus on implementing similar solutions.
Computer Security or Personnel Insecurity - The biggest lesson we learned while doing the project was defying all odds and generally understanding that many organizations in Sri Lanka are plagued with internal employees' personal insecurities about their job security and knowledge over organizational security and opportunities. General wisdom suggests organizations struggle with talent and funding; we found apart from that, the biggest hurdle is internal employees who risk the organization's security to safeguard their own job safety. This forces us to think of innovative ways to approach organizations while marketing bug bounties.
Good marketing and communication strategy - Having financial and human resources is just not enough to move forward successfully with your project unless you have a good marketing and communication strategy. A good strategy will be helpful for you to deliver your project ideas to the target audience in a very easy and effective manner. When reviewing our project progress, we felt we also should increase our marketing and communication strategy more in the upcoming months. Therefore, we have already taken a few actions for that such as recruiting professionals to create marketing materials and researching different marketing strategies that we can apply to this project and we are planning to place them in action early next year.
Make the advantages clear upfront - Based on our prior research findings, we know how bug bounties can bring an array of features for organizations, big or small. However, one of the things we learned is that as soon as we bring the plus points off but bounties compared to conventional testing, a majority of personnel take it as a threat to their comfortable security setup, even when it could potentially harm their corporate interest. One subtle change we made was to remove the comparative analysis and just pitch the advantages of bug bounties without mentioning their current methods, which seem to have better results than our previous mechanism.
Perceived Misconceptions on Security - With our prior research experience and experience from working with our local partners on the platform, the biggest lesson we learned was that regardless of the size of the organizations or the resources they have, security is a heavily misguided area. The high management responsible for making strategic decisions seems to have issues coping with the never-ending developments and solutions catering latest threats. Plus, many seem to have lost sight of the holistic nature of the security landscape, missing out on crucial perspectives such as the cost, economics behind security, and the human loop in security. These reasons eventually contribute to poor decision-making, leaving the organizations even more vulnerable.
Going the Extra Step - Bug Zero makes sure clients understand how bug bounty can help their needs. Even if bug bounty platforms are just meant to mediate between freelance bug hunters and organizations, Bug Zero has been helping organizations to understand the holistic nature. When an organization comes on board, Bug Zero helps in creating an account and getting started; we also spend time explaining the severity and the holistic nature of security. Most of the time, when organizations talk to Bug Zero, they do not have a clear idea about their requirements, and Bug Zero helps them understand them and ensure they are prepared well to work with bug hunters. We believe this is a critical step to building a more security-conscious ecosystem in this region.
They have a problem but they don't know how to fix it - Another prominent issue we have seen working with organizations so far is the inability to remediate vulnerabilities uncovered through additional security testing. This is not a unique problem for bug bounties. Many organizations lack proper security personnel, knowledge, and awareness to fix it properly. Most of the time, clients are surprised by critical vulnerabilities, but as much as they want to fix them, they lack the required knowledge, and Bug Zero has been filling in to help them. Bug Zero has been helping clients understand the severity of some vulnerabilities and fixing them as well. We believe this is an important step to make sure our client organizations are safe beyond just reporting numbers.
Unknown-unknowns - We have been dealing with a lot of entities who do not realize the problem they have and are not willing to listen to anyone outside due to various non-technical reasons. In such cases, it significantly highlighted the importance of national-level policies and guidance on vulnerability assessment and remediation. We believe our other APNIC grant for government bug bounties is catering to exactly that and hope to leave a lasting impact on the betterment of the local security ecosystem.
This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 


