TECHNICAL REPORT
| Grantee |
Universitas Swiss German (Swiss German University)
|
| Project Title | Intelligent Honeynet Threat Sharing Platform |
| Amount Awarded | USD 150,000 |
| Dates covered by this report: | 2021-12-22 to 2022-12-22 |
| Economies where project was implemented | Bangladesh, Brunei, Cambodia, Myanmar, Papua New Guinea, Sri Lanka, Timor Leste, Viet Nam |
| Project leader name |
Charles Lim
|
| Partner organization | Swiss German University has been partnering with Badan Siber & Sandi Negara (National Cyber and Crypto Agency) and Indonesia Honeynet Project (IHP) since 2018 and 2010 respectively to perform research collaboration in the area of Honeypot. |
Project Summary
Cyber security threats will continue to rise as we provide new services using the latest inventions. These newly introduced as well as existing services will pose new and unknown risks due to system vulnerabilities and other related system threats. Continuous monitoring of these threats is a must to ensure the safety and security of the running services and deploying honeypots to track these attacks will provide important and insightful information on the attacker's intention and activities. The goal of this project is to develop and implement a more intelligent honeynet threat-sharing platform that could collect, store, and add contextual information pertaining to the threat and share this threat information with the relevant organization. As more honeypot types are included, the project also intends to seek more participation in honeypot deployment and research involvement from various institutions. This project will explore machine learning-based methods to categorize threats according to their purpose, threat techniques, and procedures used during the attacks. With more public participation in deploying and sharing threats, the threats collected and enriched would be potentially used as a cyber defense platform for each of the participating organizations.
Table of Contents
- Background and Justification
- Project Implementation Narrative
- Project Review and Assessment
- Gender Equity and Inclusion
- Project Management
- Project Sustainability
- Project Communication
- Project Recommendations and Use of Findings
- Bibliography
Background and Justification
Honeypots are a decoy system designed to lure attackers so they engage in malicious activity that can be studied. They have been used by many security researchers to study attacker activities and behaviors. It is critical to be able to track and map attack patterns so that we can better anticipate their current motives and techniques used during the attack. The Indonesia Honeynet Project (IHP) has collaborated with Badan Siber & Sandi Negara (BSSN) since 2018 and has implemented more than 84 honeypots in 24 provinces across Indonesia until today.
The organizations that participated in the project include a wide range of industries, universities, and government institutions. A public portal (https://honeynet.bssn.go.id) has been developed and run to visualize the security threats detected in these honeypots, helping raise the cyber security awareness for the general public. In addition, a Cyber Security Community – Information Sharing Analysis Center (CSC-ISAC) has been established to promote a wider collaboration for all cyber security communities In Indonesia and hopefully ASEAN countries in the near future. The ultimate goal of this project is to capture more diverse security threats with more participation from different communities in different countries and translating them into threat intelligence information that can be shared with the greater cyber security community. This shared threat intelligence information would help security analysts in organizations to mitigate the security risks in a much faster and more accurate manner.
Our previous project report described how the platform has been upgraded to handle more type of honeypot-based threat data, including conpot and elastichoney, providing a wider range of threat detection. The threat data is now mapped into our own threat framework, which includes threat categories, threat purpose, and threat phase besides the common MITRE atta&k tactics and techniques. In this project, we added two honeypot types, i.e., honeytrap and RDPy, to provide an ever wider scope of detection of security threats, especially in Ethereum cryptocurrency and remote desktop services. Malware samples received from the honeypot are also stored and analyzed automatically using an open source cuckoo sandbox.
To accommodate more robust support for collecting wider range of honeypot data, we decided to upgrade our data synchronization protocol to utilize EWSposter that collects log from various honeypots and store them in the local mongoDB database. We also added mongoDB custom synchronization script from local mongoDB to our central mongoDB repository (in a cluster configuration to provide high availability) to provide more efficient and robust data collection. Performance Monitoring Dashboard (internal use only) was also added to monitor the performance of each service running in our system.
The project also added new public dashboard and custom dashboard designed for ISIF contributors, to allow each of the contributors be able to view their own honeypot data and download the data for their own use. The Public Dashboard now includes visualization of time-dependent threat behaviors, threat purposes and MITRE tactics, techniques and procedure (TTP). A new experimental graph-based attack path of the latest is also added to provide a glimpse of what will be coming in the future of our public dashboard. A new internal analysis dashboard has also been introduced to help internal researchers and analysts to visualize and analyze the data with more insights required with their own tools for additional processing if required. Data Exchange through Trusted Automated eXchange of Intelligence Information (TAXII) or Malware Information Sharing Platform (MISP) is now possible to allow threat sharing among cyber security community through Cyber Security Community – Information Sharing and Analysis Centre (CSC-ISAC).
Project Implementation Narrative
Figure 1 shows our overall system architecture, in which we have selected 6 types of important honeypots to be implemented in our system, i.e., Dionaea, Cowrie, Elasticpot, Gridpot, Rdpy, and Honeytrap.
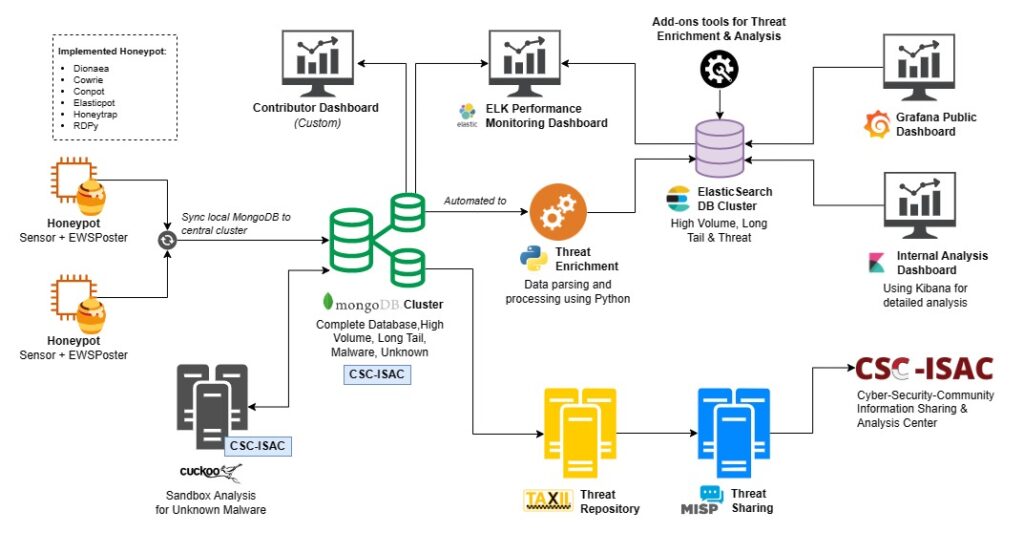
All honeypots are installed in one VM with each honeypot using its own docker container, for ease of deployment at the university premise. We began our deployment journey using a mix of several cloud services (Google, Alibaba, Digital Ocean) to test out the deployment robustness and reliability for several months. Then, we started VM deployment on academic infrastructure premise for those who have capacity to deploy their own honeypot. On the other hand, for those universities that have limited computing resources, a simple mini-PC with intel-based was deployed. As of this writing, there are now 18 universities that have participated in our collaboration and more universities are showing interest in implementing honeypots for their own use as well as contributing to the public. Research using the newer collected honeypot data, i.e. Industrial Control System (ICS) and has been published and presented in an international conference [2], [3]. In the similar way, our research team member also used Natural Language Processing (NLP) approach to categorize and map the detected Linux command-based threats into the relevant mitre att&ck TTP [4].
New automation scripts based on python has been developed and implemented to categorize and map the latest honeypot data captured into their relevant threat categories and MITRE att&ck TTP, stored in our data lake repository database. Furthermore, the categorized data has also been enriched with the results of malware analysis (if payload existed) from the cuckoo sandbox. Security analysts can create custom scripts or tools to enrich the existing data and store the enriched data into the data lake. The enriched data is now ready to be shared as a threat intelligence information using standardized threat-sharing protocols such as TAXII and MISP.
The latest version of public dashboard of CSC-ISAC have been released and they are accessible at: https://public.cscisac.org, which include the latest visualization of behavior threat map, behavior threat purpose map, mitre att&ck threat map, malware categories and the latest attack path graph. The screen capture of the public dashboard on these threats mapping can be viewed in Figure 2 and 3. An experimental graph-based attack path is also shown in the public dashboard to provide a sneak peek of what is coming in the future dashboard.
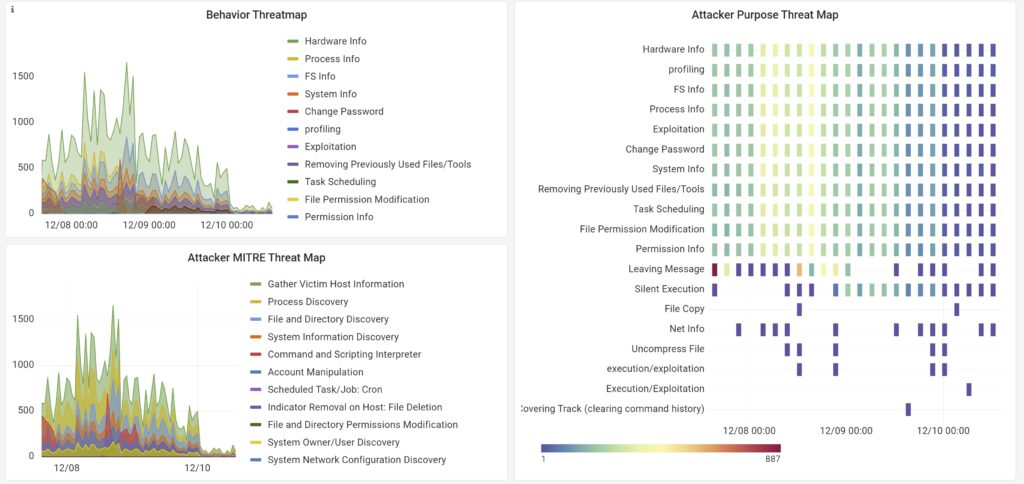
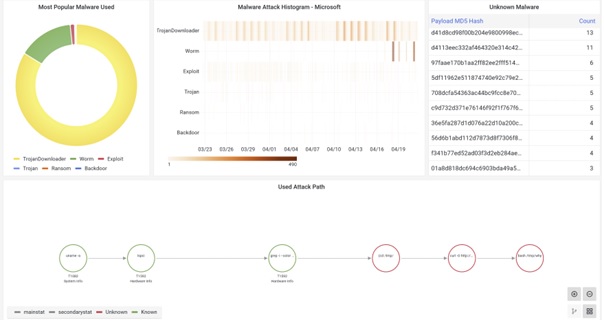
Project Review and Assessment
The project allows continuous effort from multiple institutions to perform research collaboration between ABGC institutions and build more trust between all institutions involved. We have multiple public events initiated either by each institution or collectively to create public awareness and participation in our initiative. These include participating in local and international events to raise more awareness of our research collaboration.

We conducted a hybrid event (online and offline) to share our latest research results with the public and the event has been documented and shared in LinkedIn post. In addition to researchers sharing information from the Indonesia Honeynet Project (IHP), Swiss German University (SGU) and BSSN, we also invited Tiger Graph to share with us their perspective on fraud detection using a graph database. The event provided a way to share our latest research as well as a way to collaborate with the industry on the latest threat detection technology and get feedback from the public.

The project continued the previous research [5], [6] and published a new approach of MITRE threat mapping of Linux commands found in our SSH honeypot [4]. The paper explored several possible NLP techniques to provide similarity matching during the threat mapping process. This research brings our research one step closer to a more accurate and faster threat mapping our existing honeypot data. More NLP methods will be explored to provide better performance in the future.
Other researchers explore the threats detected in our conpot/gridpot and the threats mapped into MITRE att&ck TTP both for conpot and gridpot have been submitted and presented in the the 7th IEEE International Conference on Aerospace Electronics and Remote Sensing Technology (ICARES) 2022 [2], [3].
To provide an initial knowledge and experience in using honeypot data to those universities who have participated in our project, our team of researchers conducted a series of one-day workshops that helped lecturers, researchers and students learn how to install and configure their own honeypot (in maximum 3 hours’ time) and how to visualize and analyze the honeypot data they captured during the workshop (also in maximum 3 hours’ time). Figure 6 shows the one-page flyer used to invite the relevant lecturers and students to the event at Universitas Putra Batam (UPB) and Institut Informatika dan Bisnis (IIB) Darmajaya.

Figure 7 shows the next 2 universities’ one-page invitation flyer for Universitas Bina Darma (UBD) dan Universitas Nusa Mandiri (UNM).

Each participant was given their own cloud VM and learned how to visualize and analyze their own honeypot data right from their individual browser, which provided a very lightweight experience in the learning process.
Some updates on the above events can be accessed at the following LinkedIn posts:
- https://www.linkedin.com/posts/charles-lim_swissgermanuniversity-indonesiahoneynetproject-activity-7024651429562773504-q1ih (UPB)
- https://www.linkedin.com/posts/charles-lim_swissgermanuniversity-indonesiahoneynetproject-activity-7027227633771831296-GvLK (IIB Darma Jaya)
- https://www.linkedin.com/posts/charles-lim_honeypot-swissgermanuniversity-ubidar-activity-7033652492991123456-UP3U (UBD)
- https://www.linkedin.com/posts/charles-lim_today-we-have-the-privilege-to-share-our-activity-7047021037909127168-bmHe (UNM)
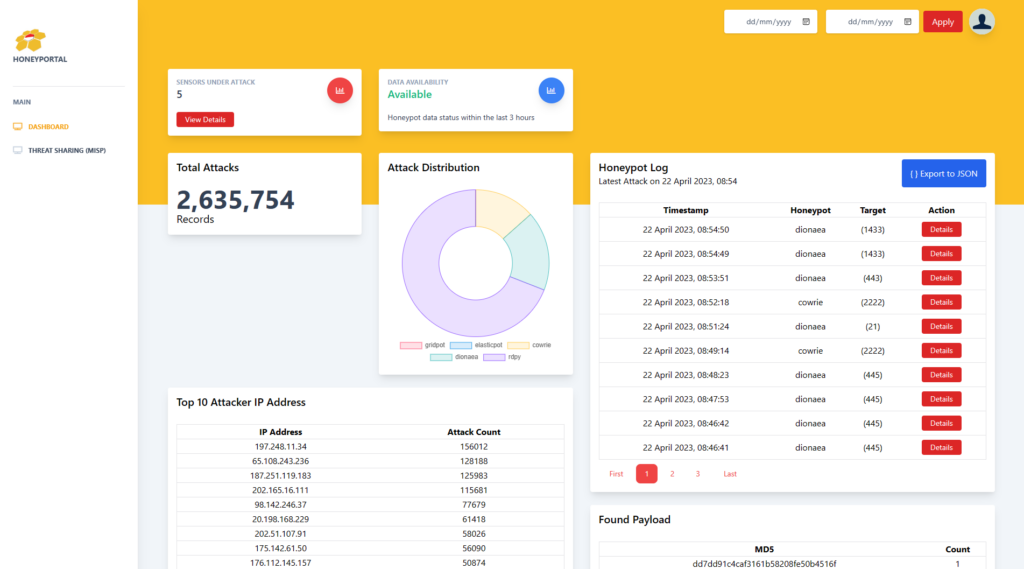
The participants can either use their own honeypot data or download from the honeyportal, a custom portal dedicated for each of the project contributors. Figure 8 shows one of the contributor honeyportal, in which they can view the simple statistics of the source of attacks, honeypots (up or down) and daily or range of data to be shown and downloaded.
For the cyber security community who needs to pull daily or range of dates of the honeypot data, they can use TAXII or MISP to achieve their goals. Figure 9 and 10 show the screen capture of our MISP Threat Sharing Platform, used as a platform for public sharing of our enriched honeypot data. The threat data will be inserted daily (can be configured more often) to MISP database from our enriched data stored in our data lake.
One of the most important lessons learned during the implementation or deployment is the necessity of using the proper ready-to-use documentation to help user accelerate their own deployment with minimum support. Hence, key documentation includes: Design Documentation, User Manual (include detail deployment steps) and Frequently Asked Questions (FAQ) are very helpful to deployment and users who deploy their honeypot in their own premises. Since software will always have bugs or other problems, we always try to work with the university team that is willing to work together to solve the pending problems. As the number of honeypot sensors continues to increase, obviously we need more people to handle the possible problems that might occur during the operation. For this, we plan to migrate our public portal to the cloud service provider, to increase access performance and to reduce hardware maintenance efforts that might appear during the operation. At the same time, dedicated personnel need to be allocated to monitor and possibly maintain the running system to better serve the community.
Gender Equity and Inclusion
In our research team, we have five masters students, two alumni (masters) and one support admin. In addition, our research team also includes at least three women and five male bachelor students, depicting our commitment for gender equality inclusion. We structured the team such that Bachelor students and young government officials will be mentored by master students. This type of inclusion provides us an opportunity to understand different views when we are working with a diverse set of students from different provinces or regions, either locally or internationally.
Project Management
As our project grew to include more diverse team members, we shifted from the use of online spreadsheet tools to manage project to online project management online tools such as asana, shown in Figure 11.
Our weekly meeting on Wednesday is still conducted online and the meeting focuses on 2 major issues: Design and Implementation. The meeting will be led by co-leader to discuss update from members and issues pertaining to the above 2 major issues. Figure 12 shows the leader and co-leaders who will lead and co-lead the project from time to time.

In addition, each of the groups also has its own separate online weekly meetings and recaps its results in a minute of meeting documentation, as shown in Figure 13. Our research assistants (scholarship funded by ISIF) participate in the weekly meetings, ensuring progress and achieving the intended results.
Project Sustainability
To maintain the sustainability of this project, starting year 2021, the project initiated and established an independent cyber security community (Cyber Security Community - Information Sharing and Analysis Center, i.e., CSC-ISAC) to maintain the future communication and services to all the participating members in this project. In the future, this non-profit community-based organization will receive members' donations to continuously share threat intelligence with the public.
Project Communication
To raise the public awareness, SGU uses SGU’s own Digital Clinic Hybrid Seminar on 29 September 2022 to expose to public our latest research results, as shown in Figure 14.

Members from IHP and BSSN, including commercial company, Tiger Graph, also participated in raising public awareness on using graph technology in the area of Threat Intelligence. We all agreed and learned that it is very useful to explore the possibility of using graph databases in threat detection and analysis but we also realized that it is quite a long way to go to realize how to detect and match the new unknown threats using graph analytics. This event achieved one of our key goals, in which academic, business, government and community collaborate and share their latest insights together in a event to raise the public awareness on cyber security. This also provides an opportunity for SGU to top undergraduate students from all universities in Indonesia, and this raises awareness of our ISIF Asia research on our campus. Figure 15 shows our media communication to the public to recruit fresh graduates to apply and join the scholarship of our Cyber Security Master Program of SGU.

In addition, the project also conducted 4 different workshops at 4 different universities (UPB, IIB Darma Jaya, UBD and UNM) around Indonesia. These workshops are designed to help to develop each of the university lecturers and their students’ interest to do research using honeypot data they collected in their university. The media communication (flyers) for the events at each of the universities are shown in Figures 6 and 7.
Project Recommendations and Use of Findings
Our research has been submitted, presented and published at different International Conferences in 2022:
- Threat Analysis on Industrial Control System Based on Attacker's Behaviours using Honeypots – submitted and presented on the 2022 IEEE International Conference on Aerospace Electronics and Remote Sensing Technology (ICARES) [2].
- Mapping Threats in Smart Grid System Using the MITRE ATT&CK ICS Framework - submitted and presented on the 2022 IEEE International Conference on Aerospace Electronics and Remote Sensing Technology (ICARES) [3].
- Mapping Linux Shell Commands to MITRE ATT&CK using NLP-Based Approach - published in ACM Proceeding of The 4th International Conference on Electrical Engineering and Informatics (ICELTICs) 2022 [4].
The first paper, “Threat Analysis on Industrial Control System Based on Attacker's Behaviours using Honeypots,” explored the security threat found in Industrial Control System and mapped to our own Threat Categorization mapping and MITRE ATT&CK mapping.
Similarly, the second paper, “Mapping Threats in Smart Grid System Using the MITRE ATT&CK ICS Framework,” focused on the security threats found in grid system-based honeypot to MITRE ATT&CK TTP, in particular modbus dan s7comm protocols.
Finally the third paper “Mapping Linux Shell Commands to MITRE ATT&CK using NLP-Based Approach” paper, we shared our latest exploration and insights of mapping Linux shell command efforts into MITRE ATT&CK TTP using NLP approach.
Several methods of NLP-based algorithms, such as Bag of Words, TF-IDF, and pre-trained Word Embeddings, were used to find the most promising methods to provide matching of commands to MITRE TTP. With the right method, we believe we can map these commands into the right and accurate MITRE TTP with the shortest possible time.
With more research and deeper analysis of the honeypot data collected, we hope to share the anonymized and enriched dataset to cyber security community including researchers either directly using TAXII or MISP, or downloadable datasets from a public portal in CSC-ISAC web site.
Bibliography
[1] L. Spitzner, “The honeynet project: Trapping the hackers,” IEEE Secur. Priv., vol. 1, no. 2, Art. no. 2, 2003.
[2] A. H. Nursidiq and C. Lim, “Threat Analysis on Industrial Control System Based on Attacker’s Behaviors using Honeypots,” in 2022 IEEE International Conference on Aerospace Electronics and Remote Sensing Technology (ICARES), IEEE, 2022, pp. 1–6.
[3] A. B. Izzuddin and C. Lim, “Mapping Threats in Smart Grid System Using the MITRE ATT&CK ICS Framework,” in 2022 IEEE International Conference on Aerospace Electronics and Remote Sensing Technology (ICARES), IEEE, 2022, pp. 1–7.
[4] Y. Andrew, C. Lim, and E. Budiarto, “Mapping Linux Shell Commands to MITRE ATT&CK using NLP-Based Approach,” in 2022 International Conference on Electrical Engineering and Informatics (ICELTICs), IEEE, 2022, pp. 37–42.
[5] Ryandy, C. Lim, and K. E. Silaen, “XT-Pot: EXposing Threat Category of Honeypot-Based Attacks,” in Proceedings of the International Conference on Engineering and Information Technology for Sustainable Industry, in ICONETSI. New York, NY, USA: Association for Computing Machinery, 2020. doi: 10.1145/3429789.3429868.
[6] R. Djap, C. Lim, K. E. Silaen, and A. Yusuf, “XB-Pot: Revealing Honeypot-based Attacker’s Behaviors,” in 2021 9th International Conference on Information and Communication Technology (ICoICT), Yogyakarta, Indonesia: IEEE, 2021, pp. 550–555. doi: 10.1109/ICoICT52021.2021.9527422.
This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 


